Over the past year, open-source package registries have been hit by a series of high-profile supply chain attacks, with npm among the most heavily targeted. From multiple waves of the self-propagating Shai-Hulud campaign, which compromised hundreds of legitimate packages by stealing maintainer credentials and injecting malware to exfiltrate secrets, to the state-sponsored Contagious Interview operation that weaponizes fake recruiter interactions, the pattern is clear:
Supply chain attacks are no longer isolated incidents. They are often coordinated, long-running campaigns.
That shift creates a visibility gap. Teams may identify an individual malicious package, but still lack clarity on whether it is part of a broader campaign, how that campaign is evolving, or whether newly publish…
Over the past year, open-source package registries have been hit by a series of high-profile supply chain attacks, with npm among the most heavily targeted. From multiple waves of the self-propagating Shai-Hulud campaign, which compromised hundreds of legitimate packages by stealing maintainer credentials and injecting malware to exfiltrate secrets, to the state-sponsored Contagious Interview operation that weaponizes fake recruiter interactions, the pattern is clear:
Supply chain attacks are no longer isolated incidents. They are often coordinated, long-running campaigns.
That shift creates a visibility gap. Teams may identify an individual malicious package, but still lack clarity on whether it is part of a broader campaign, how that campaign is evolving, or whether newly published packages tied to the same operation will impact them next.
Introducing the Threat Intel Page
Today, we are introducing a new Threat Intel page in the Socket dashboard, designed to close that gap.
Until now, Socket’s threat coverage has centered on the Threat Feed, which surfaces newly detected malicious packages identified by our AI scanner and validated by our threat intelligence team. While this remains a critical signal, it reflects only a point in time.
The new Threat Intel page expands beyond individual detections, starting with a dedicated Campaigns view that tracks active supply chain attack campaigns as ongoing entities and shows whether your organization is affected.
Campaigns View: Know When You Are Impacted
The Campaigns view lists all currently active supply chain attack campaigns and clearly shows whether your organization is Safe or Impacted.
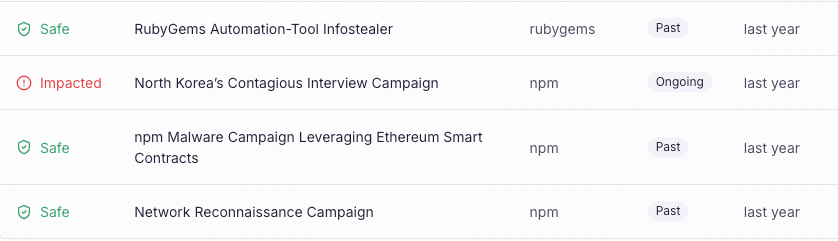
When a campaign affects your organization, you can immediately see which repositories are involved and which packages are part of the campaign. Selecting a campaign opens a dedicated detail page with additional context from Socket’s in-house threat intelligence team, along with direct links to impacted repositories in your dashboard so you can investigate and respond quickly.
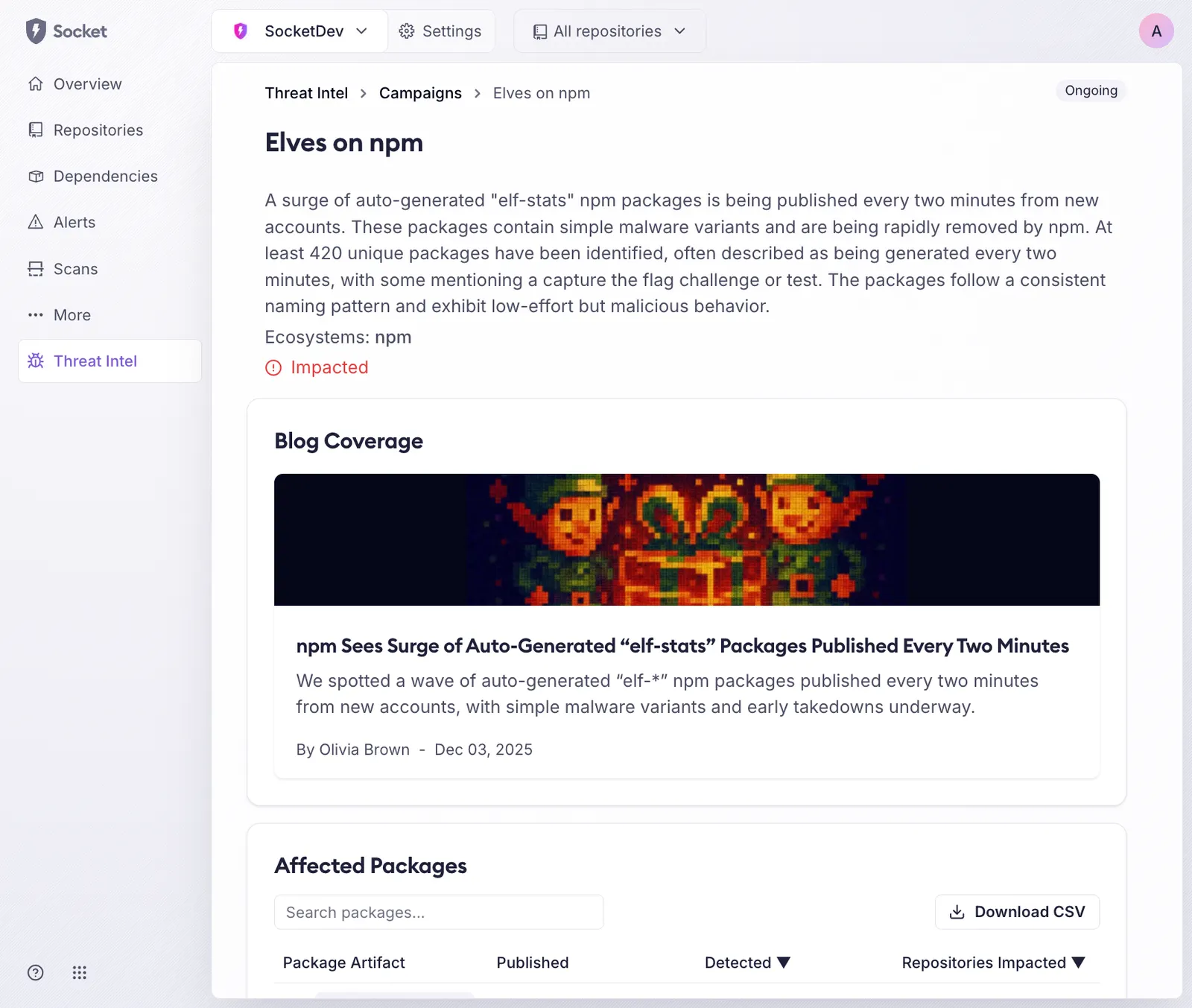
This view is designed for the moment when a new supply chain attack emerges and the first question is simple: are we affected?
Instead of scanning advisories, cross-referencing package names, or running one-off scripts that may already be out of date, teams can log into the dashboard and get an immediate answer. Campaigns are continuously updated as new packages are linked to the same operation, and your organization’s impact status updates automatically as your dependency graph changes.
Campaign Context, Directly on Package Pages
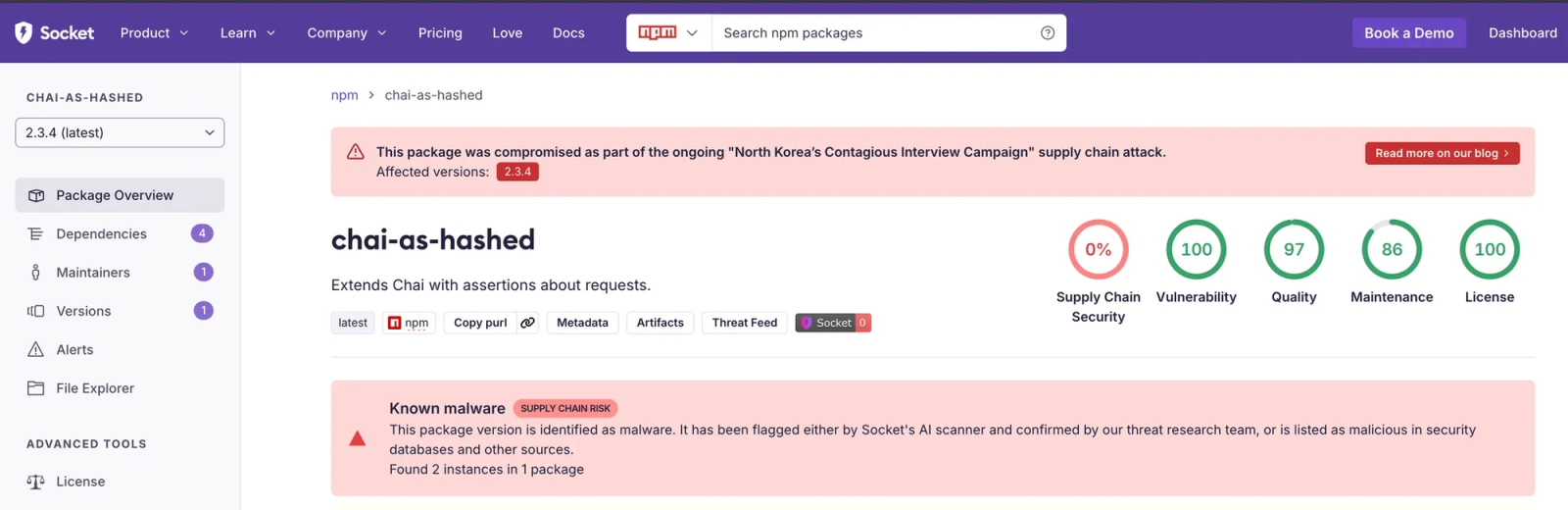
Campaign tracking does not stop at the Campaigns view. When a package is linked to an active supply chain attack campaign, that context now appears directly on the package’s detail page in the Socket dashboard.
At the top of the page, a prominent warning banner indicates that the package was compromised as part of an ongoing campaign, clearly naming the campaign and calling out the affected versions. This makes it immediately obvious when a package is not just malicious in isolation, but part of a larger, coordinated attack.
From there, teams can drill into the same package details they already rely on, including version history, dependency information, and Socket’s risk signals across supply chain security, vulnerabilities, quality, maintenance, and licensing. A dedicated malware alert section provides additional detail on how the package was identified and what type of risk it poses.
Designed for Fast Investigation and Response
The Threat Intel page is built to help organizations move quickly from awareness to action.
- Filter campaigns by ecosystem such as npm, PyPI, or Maven to focus on what matters to your stack
- View affected packages with publish dates, detection dates, and impacted repositories
- Navigate directly from campaign context to package details and remediation workflows
- Export campaign and package data for reporting or internal analysis
By grouping related packages under a single campaign, the view reduces noise and helps teams prioritize response based on actual exposure.
Tracking Campaigns as Supply Chain Attacks Emerge#
Campaign tracking is available today for all users as part of the new Threat Intel page in the dashboard. It is the first step in a broader Threat Intel experience within Socket.
Over time, this page is designed to expand to include additional forms of threat intelligence such as attacker techniques and behaviors, infrastructure indicators, and richer campaign-level context that extends beyond individual packages. We also plan to ship public API endpoints in the near future, enabling teams to integrate campaign intelligence directly into their own security workflows.
The goal is to help teams understand not just what was detected, but how these threats evolve and what that evolution means for your environment. You can explore active and past campaigns today on the Threat Intel page of the Socket dashboard.