Building on the success of the 2nd annual Security Operations Centre (SOC) at Cisco Live Melbourne (Asia Pacific Japan) 2024, the executive team supported the first SOC for Cisco Live San Diego (Americas) and invited the team back for 20025. Planning a successful SOC begins with a strong collaboration with the Network Operations Centre (NOC), which assigns a team of engineers to construct the network in the weeks leading up to the conference.
Check out the CiscoTV interview of Shaun outside the SOC.
The core missions of the SOC were:
- Protect: Safeguard the network from threats and attacks, both internal and external
- Educate: In…
Building on the success of the 2nd annual Security Operations Centre (SOC) at Cisco Live Melbourne (Asia Pacific Japan) 2024, the executive team supported the first SOC for Cisco Live San Diego (Americas) and invited the team back for 20025. Planning a successful SOC begins with a strong collaboration with the Network Operations Centre (NOC), which assigns a team of engineers to construct the network in the weeks leading up to the conference.
Check out the CiscoTV interview of Shaun outside the SOC.
The core missions of the SOC were:
- Protect: Safeguard the network from threats and attacks, both internal and external
- Educate: Inform and engage attendees through SOC tours and blog content
- Innovate: Develop and implement new integrations, processes, workflows, and automations
The SOC team worked diligently to detect, pinpoint, and assist in the remediation of threats whenever an attendee’s device or account was identified as compromised or insecure.

The SOC at Cisco Live SOC was successfully deployed in just 12 hours over 1 ½ days, demonstrating extensive prior planning and specialized expertise. This rapid setup was enabled by several key factors
- The deployment of the “SOC in a Box,” a custom hardware solution refined through years of experience at the RSAC Conference, enabling rapid connectivity with the Cisco Live NOC, Splunk Enterprise Security, and the Cisco Security Cloud.
- Drawing upon proven expertise, workflows, and procedures from the RSAC 2025, Cisco Live San Diego, and GovWare 2025 SOCs, with many veteran engineers providing both on-site deployment and dedicated remote support. We also brought in new SOC analysts for Tier 1 interns.
- Integrating advanced innovations and security practices developed while safeguarding the Black Hat network, recognized as the world’s most hostile environment.
- The partnership with Endace, a highly skilled full-packet capture provider, whose experience in the 2025 SOC was critical and extended to their commitment for Cisco Live Melbourne.
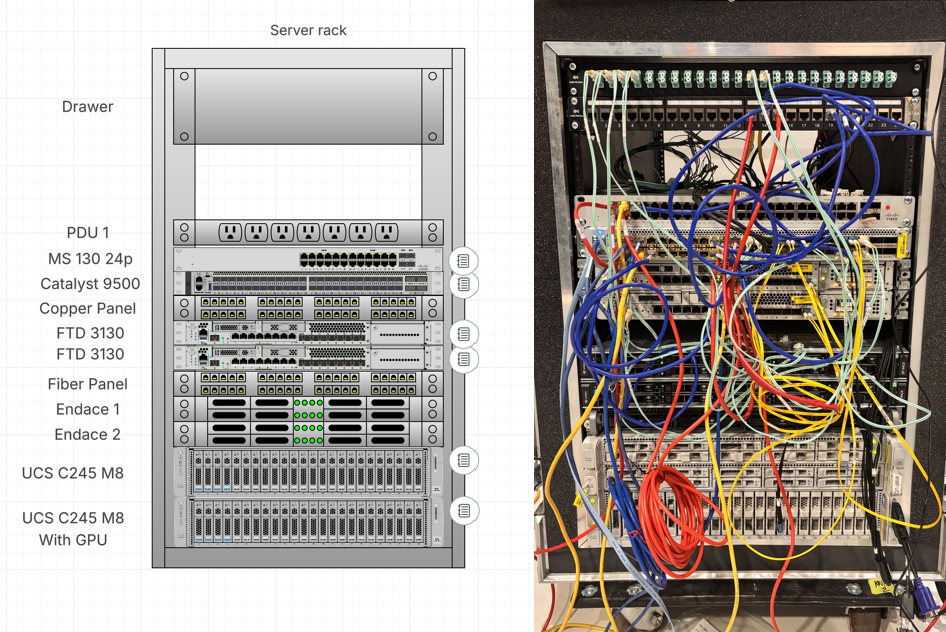
The SOC Architecture
The SOC team worked with the NOC to connect the ‘SOC in the Box’, Secure Access virtual appliances for Domain Name Service (DNS), and received a Switched Port Analyzer (SPAN) of the network traffic.
The SOC team deployed the EndaceProbe packet capture platform to record all network traffic, enabling full investigation of any anomalous behavior. The EndaceProbe platform also generated metadata (including Zeek logs) into the Splunk Enterprise Security Platform. File content was reconstructed on the wire on the EndaceProbe, filtered, and streamed to Splunk Attack Analyzer (and on to Secure Malware Analytics) for sandboxing and analysis.
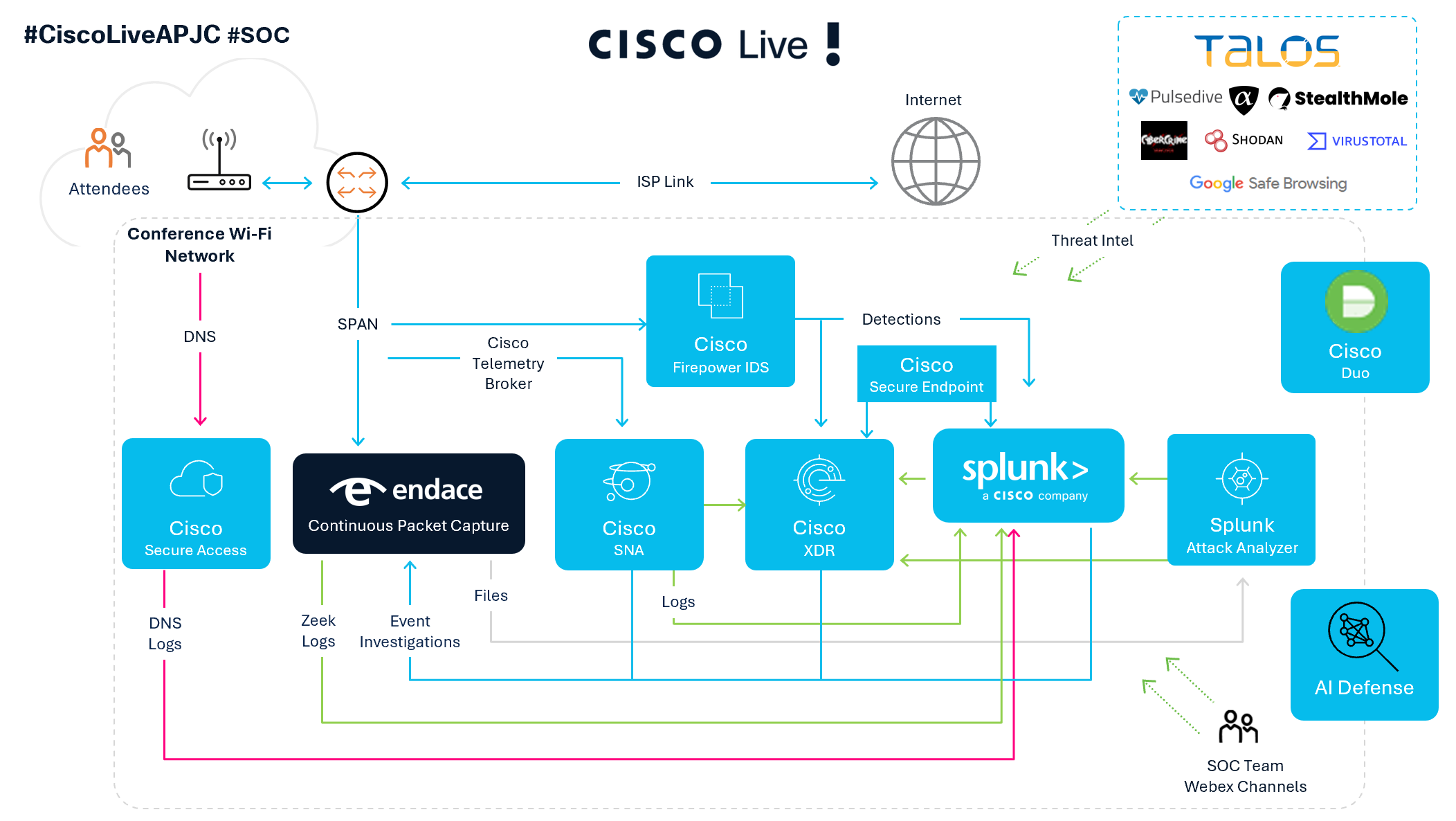
The SOC team used Duo Central for Single Sign-On access to the tools, both on-premises and in the cloud, executing from the first customer experience at Black Hat.

By leveraging cloud-based solutions like XDR and Splunk Cloud, this also minimized the amount of work that was needed in a very tight setup window.
With the successful rapid deployment, we had time for team training on investigations and escalations to Tier 3 / incident responder and management.

Configurations and other data were already ready to go from previous events as well, including dashboards in Splunk, from the innovations of Ivan Berlinson.
Incidents were investigated in XDR, with threat intelligence provided by Cisco Talos, and licenses donated by alphaMountain, Pulsedive, and StealthMole, along with community sources.
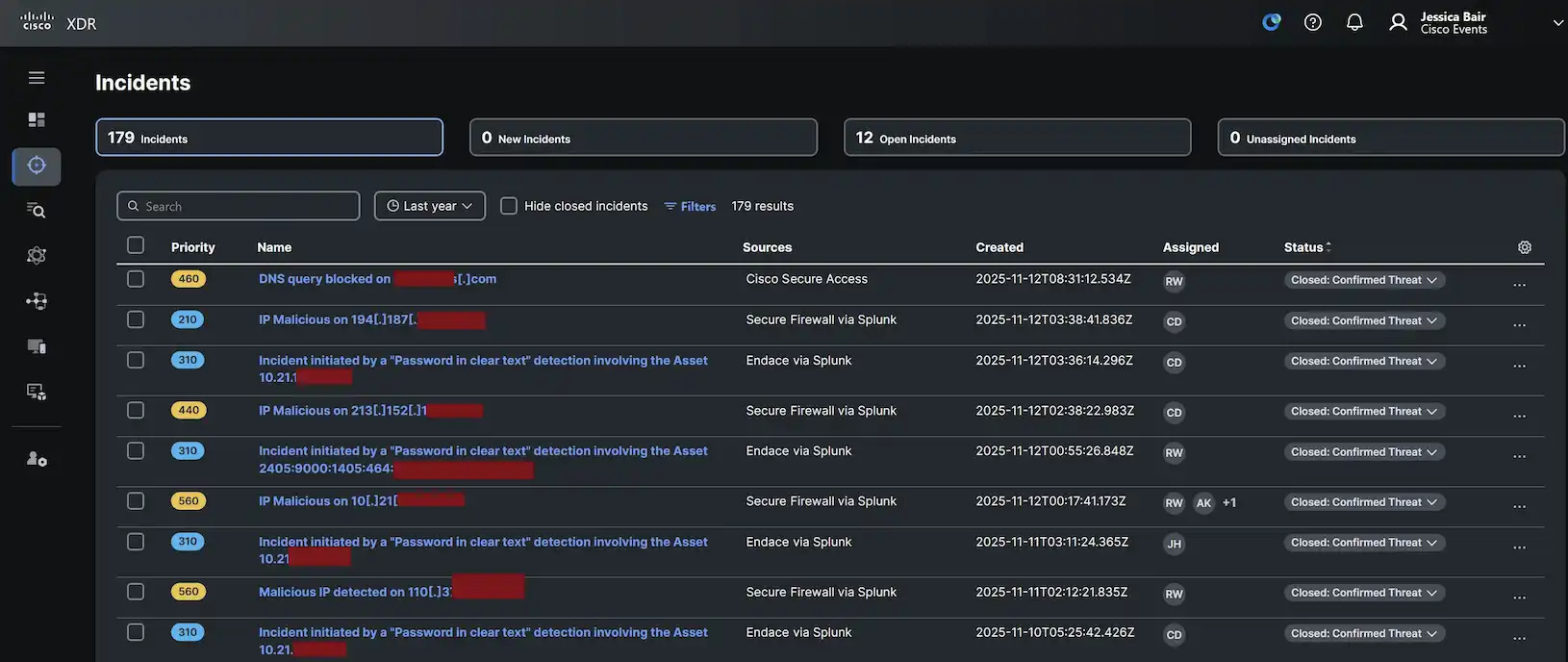
Tier 3 experts within Splunk’s Threat Response team, dedicated to safeguarding Splunk Cloud’s infrastructure, leveraged Splunk Enterprise Security, with Incidents escalated from Cisco XDR by our Tier 1 & 2 analysts.
The Cloud Protection Suite was deployed to secure the SOC cloud infrastructure, along with Cisco Identity Intelligence.
The Statistics
Statistics are always a popular part of the SOC Tours. Below are the stats from this year’s event.
| Attendees (Cisco Live) | 6,200 |
| Total packets captured (Endace) | 30.2 billion |
| Total logs captured (Splunk) | 1.26 billion |
| Total sessions (Endace) | 256.7 million |
| Total unique devices (Firewall) | 7,539 |
| Total packets written to disk (Endace) | 26.9 TBs |
| Total logs written to cloud (Splunk) | 1.02 terabytes |
| Peak bandwidth utilization (Endace) | 3.76 Gbps |
| DNS Requests (Cisco) | 61.4 million / 938 blocked |
| Total clear text username/passwords (Endace) | 1,525 |
| Unique devices / accounts with clear text usernames / passwords (Endace) | 34 |
| Files sent for malware analysis (Endace) | 378k file objects reconstructed by Endace. 13,763 sent to Splunk Attack Analyzer 2,914 sent to Secure Malware Analytics |

SOC Findings and Lessons Learned
The SOC team focuses on continuous innovation and takes time to document their experiences for the edification and education of the community.
Check out the blogs below from the engineers who worked inside the SOC in Melbourne. For example, Ryan MacLennan created an AI model to find domain generated algorithms at the Cisco Live AMER Security SOC. It can run on the new ‘SOC in a Box’ GPUs on the UCS M8. Ryan gave the model to Splunk Research, who published for the community.
- Firewall and Splunk ESCU Integration at the Cisco Live Melbourne SOC
- Cisco Live Melbourne Case Study: Investigation into a High Traffic Spike
- Cisco Live Melbourne Case Study: Cisco Live TME experience and DDOS
- Delivering on the Mission to Educate: A Recap of the Cisco Live Melbourne 2025 SOC Tours
- Beyond the First Clue: XDR Forensics at Cisco Live APJC 2025
- Splunk in Action: From SPL to PCAP
- Hunting Compromised Credentials in Real Time Integrating StealthMole with Cisco XDR at Cisco Live Melbourne
- Have You Seen My Domain Controller?
- In Splunk Empty Fields May Not Be Null
- A Newbie’s Perspective: Curiosity to Confidence – My SOC Story
- Endace: What We Learned After Five Incredible SOC Events
- Endace: Cisco Live APJ 2025: Endace full packet capture finds Active Directory credentials
- Endace: Cisco Live APJ 2025: Optimizing Analysis of Reconstructed Packet Data
- Endace: Cisco Live APJ: Cleartext Passwords and Always on Packet Capture
Acknowledgements
A heartfelt thank you to the engineers whose expertise made the Cisco Live Melbourne 2025 SOC a tremendous success, effectively safeguarding the network and providing valuable education to attendees.

Network Operations Center Liaisons
- Freddy Bello, Andy Phillips, Chris Augulewicz and Scott Neuman
Cisco Security and Splunk SOC Team
- Innovation / Cloud Protection Suite: Ryan Maclennan
- Cisco Security Integrations: Ivan Berlinson
- Splunk Integrations: Duane Waddle
- Splunk Incident Responder: Brendan Kuang
- Breach Protection Suite: Robin Wei, Cam Dunn, Hanna Jabbour and Pradnya Padaki
- User Protection Suite: Justin Murphy and Jaki Hasan
- Firewall and Security Cloud Control: Adam Kilgore and Apaar Sanghi
- Remote support: Ben Greenbaum
Endace SOC Team
- Co-SOC Leader: Steve Fink
- Endace VP Product: Cary Wright
- Endace Engineering: Caleb Millar, Daniel Lawson and Peter Watt
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media