Securing a live conference can be like threat hunting on hard mode. You’re dealing with diverse devices, temporary networks, guest credentials, and thousands of users, all while threats need to be identified and addressed in real-time. Effective threat hunting in this environment requires more than just detecting anomalies; it demands the ability to quickly pivot from high-level alerts to granular packet-level forensics. During my recent work protecting GovWare 2025, I discovered that integrating Splunk Enterprise and Splunk Attack Analyzer (SAA) with Endace created a powerful threat hunting workflow that bridged the gap between security analytics and network forensics. This combination transformed our ability to not only identify…
Securing a live conference can be like threat hunting on hard mode. You’re dealing with diverse devices, temporary networks, guest credentials, and thousands of users, all while threats need to be identified and addressed in real-time. Effective threat hunting in this environment requires more than just detecting anomalies; it demands the ability to quickly pivot from high-level alerts to granular packet-level forensics. During my recent work protecting GovWare 2025, I discovered that integrating Splunk Enterprise and Splunk Attack Analyzer (SAA) with Endace created a powerful threat hunting workflow that bridged the gap between security analytics and network forensics. This combination transformed our ability to not only identify suspicious activity but to rapidly investigate and validate threats with definitive evidence. In this post, I’ll share how this integration worked in practice and the key lessons I learned about threat hunting at scale.
We leveraged Splunk Attack Analyzer’s robust API to connect to Endace, an advanced network recording tool that provides packet-level visibility into network activity. Endace (via Zeek) automatically submitted suspicious files and URLs (aka “resources”) detected in network traffic to SAA. Many of the files submitted were benign, so it was eye-catching when SAA flagged a file with a score of 100. The file in question was a zip file that contained a malicious executable file .exe. We were particularly interested in running this file through Cisco’s SMA’s (Secure Malware Analytics) sandbox which we integrated with SAA. In fact, 22 out of the 28 detections for this file came from this sandbox, formerly known as Threat Grid. These detections play a vital role in the analysis, as there is some detection logic applied.
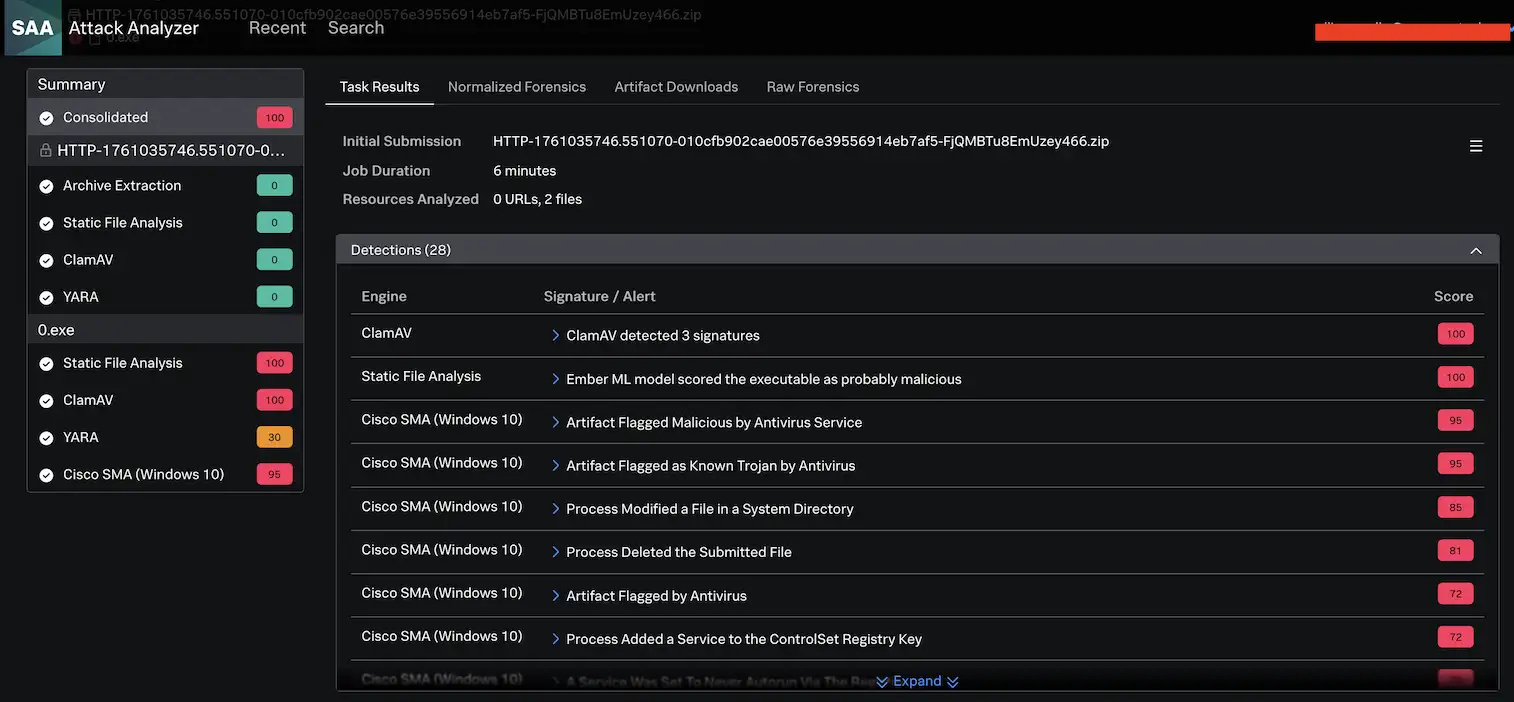
When looking at the “Normalized Forensics” tab for this task, of particular interest is the “Strings & Configs” tab which contains macro code that was extracted or emulated. For this document we could see that SAA extracted a string for the website “sogou[.]com”, a legitimate Chinese search engine and technology company. However, another string that was extracted included “Gh0st Update”, which has been observed in the infamous Gh0st RAT malware.
Gh0st RAT is notorious for establishing persistence to ensure it runs after a system reboot. This often involves modifying registry keys or creating services. SAA’s analysis revealed textbook Gh0st RAT tactics:
- Persistence through registry and service manipulation
- Evasion via Armadillo packing and file obfuscation
- Suspicious memory operations suggesting code injection
- Clear C2 communication attempts
The 22 detections from our Cisco sandbox painted an unmistakable picture of advanced malware behavior.
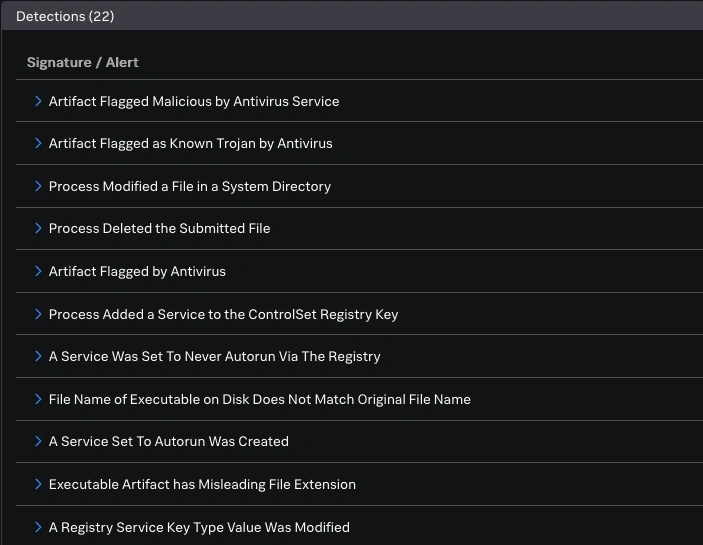
While the SAA forensics results clearly indicated C2 attempts, the network activity logs within SAA initially showed only internal DNS and DHCP traffic. This was a crucial point of investigation: if the RAT was trying to “phone home,” where was the external communication? This led us to pivot from the sandbox’s internal view to our broader network logs in Splunk Enterprise.
With little visibility into endpoints, our DNS and DHCP logs became our primary source of truth. We knew the Gh0st RAT variant likely employed a Domain Generation Algorithm (DGA) to find its C2 server, meaning it would attempt to resolve randomly generated domains, often resulting in NXDOMAIN (Non-Existent Domain) responses.
We meticulously sifted through all NXDOMAIN responses from the conference guest network during the relevant timeframe. Many were typical noise: reverse DNS lookups, service discovery attempts from attendees’ corporate devices, or legitimate services that simply weren’t resolvable on our guest network. Admittedly, this is where our hunt came to an end as we determined that one of our engineers had submitted this file as a test. However, it was a fun rabbit hole to wander down, and it gave us some ideas about the capabilities of our tools, as well as indicators to be on the lookout for.
From Warm-Up to Real Threat: Uncovering Active C2 Communication
After the warm-up exercise with the test file, we shifted our focus back to the continuous stream of submissions from Endace to SAA. This time, a URL submission caught our attention with a score of 75, primarily flagged for “Social Engineering” indicators. While not as dramatic as our earlier score of 100, a combination of factors made this worth investigating: particularly the domain’s recent creation date, which added another 15 points to its risk score. Recently created domains are often a hallmark of attackers setting up new infrastructure for campaigns.
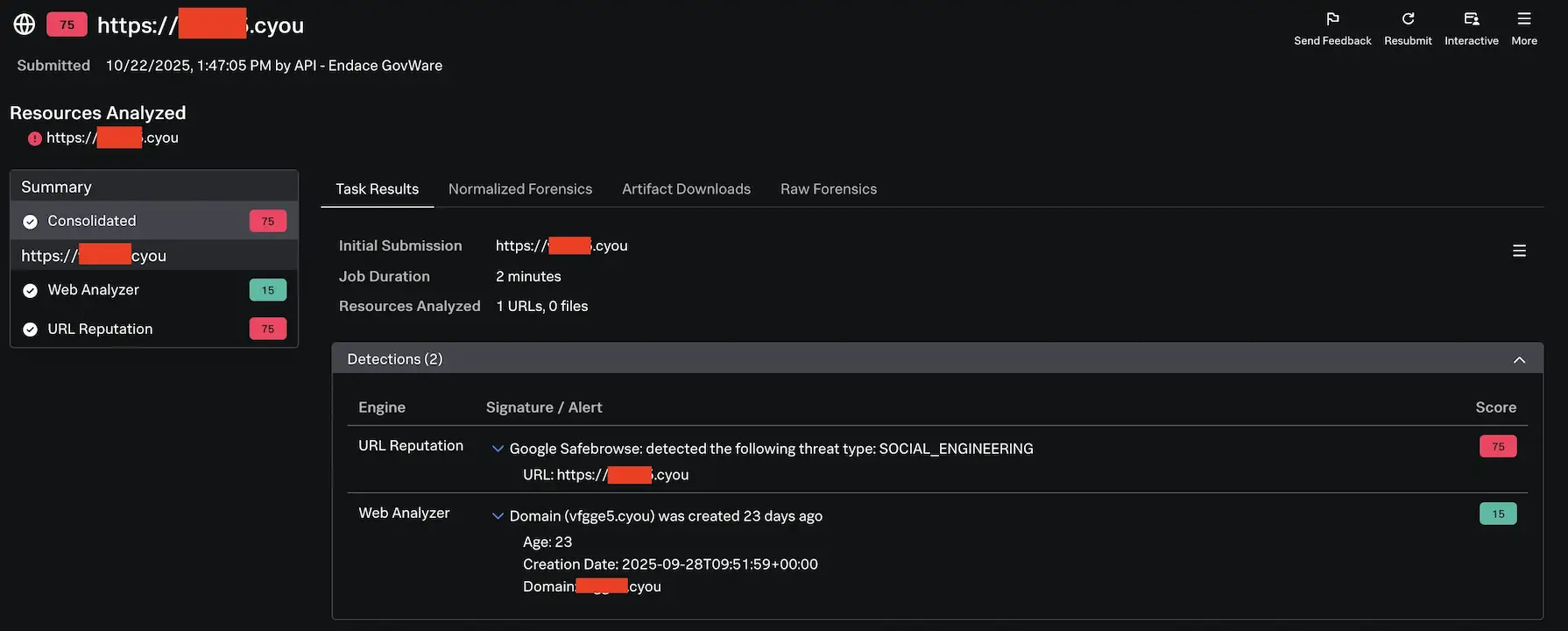
To expand our investigation beyond SAA’s initial analysis, I pivoted to VirusTotal for additional context on the domain. This cross-referencing revealed two IP addresses associated with the suspicious domain, with one particularly standing out: 103.235.46[.]102. This IP immediately raised red flags in our threat intelligence sources.
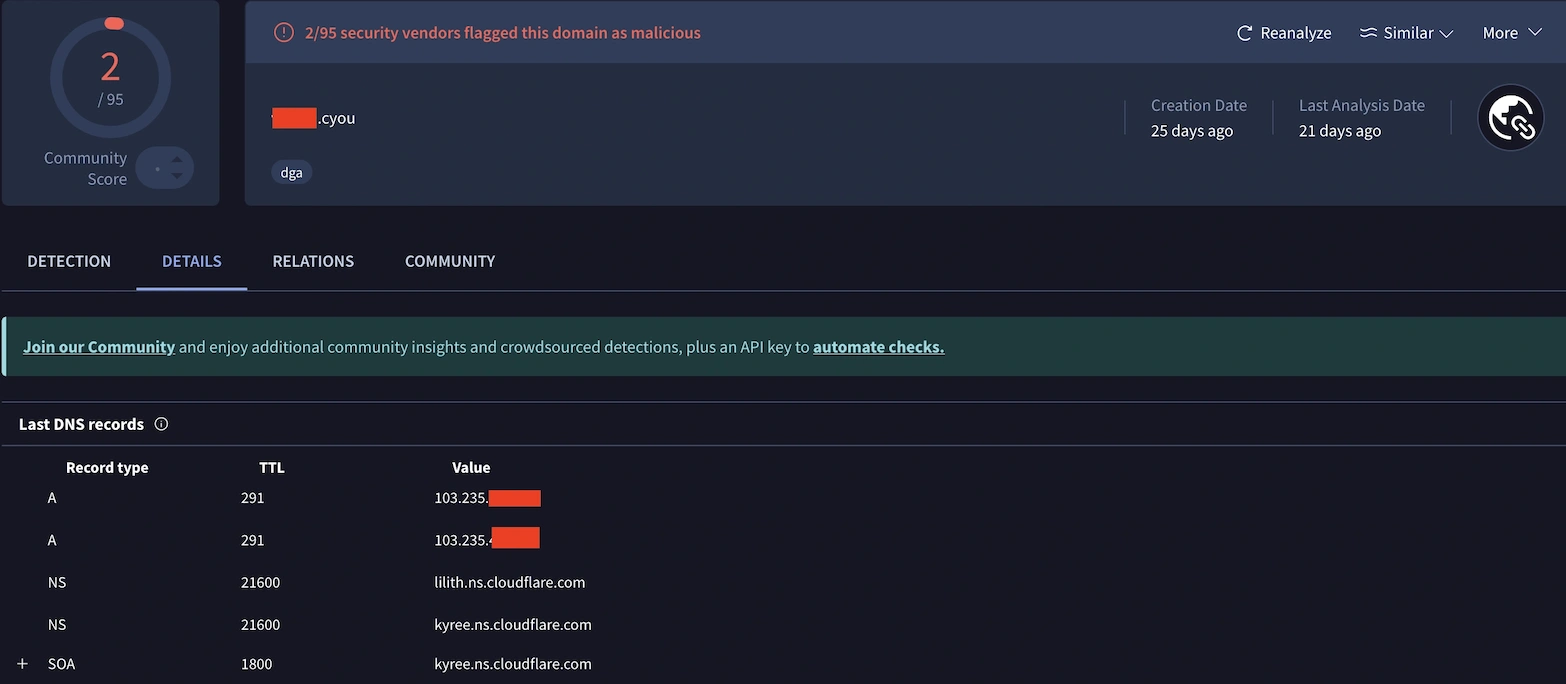
Connecting the Dots: From Suspicious Domain to Known Threat Actor Infrastructure
The IP address 103.235.46[.]102 wasn’t just another suspicious indicator. Our Talos Threat Hunter working alongside us pointed out that it had a documented history as command-and-control infrastructure. According to Google Cloud’s threat intelligence reporting, this IP was previously associated with a ViewState deserialization zero-day vulnerability campaign, where it served as an attacker-controlled node for C2 operations. This context transformed our investigation from a routine suspicious domain check into a potential active threat scenario.
Leveraging Endace’s packet-level visibility, we were able to definitively answer the critical question: was anyone on our conference network actually communicating with this known-bad infrastructure? The answer was concerning, as I found three distinct hosts on the guest network that showed active communication patterns with 103.235.46[.]102. Endace’s forensic capabilities allowed us to not only confirm the connections but also examine the nature and timing of the traffic, providing crucial evidence for our incident response.
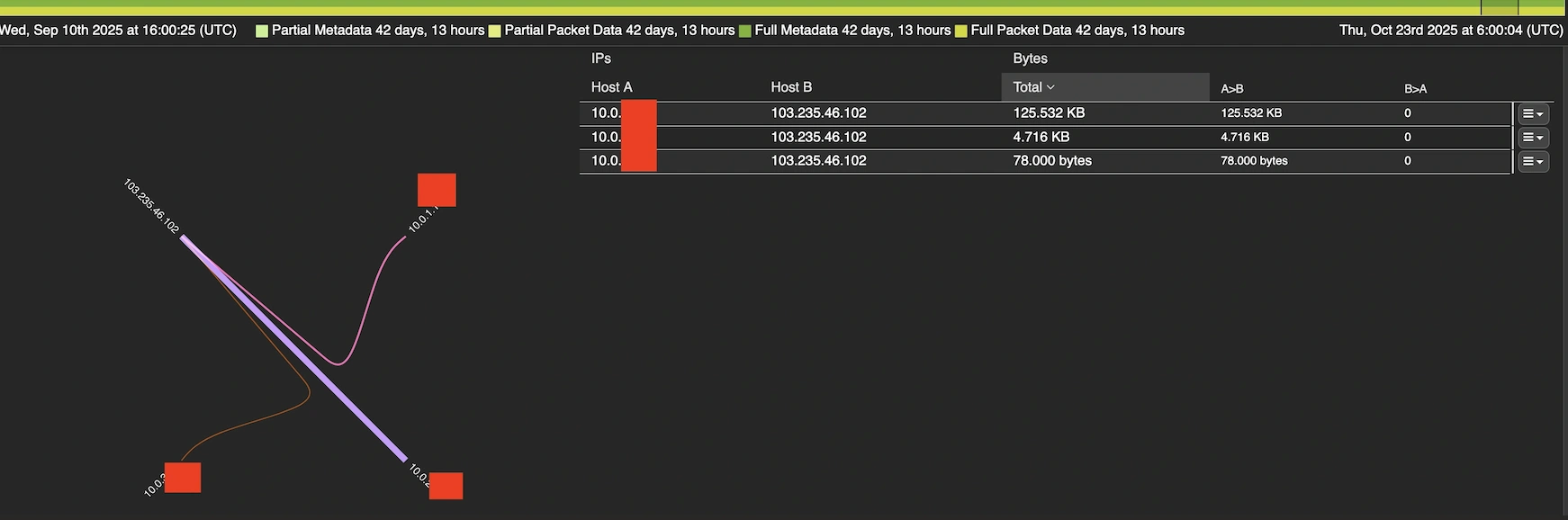
Rapid Response: From Detection to Mitigation
With concrete evidence of conference devices communicating with known C2 infrastructure, we immediately escalated from investigation to containment. The combination of SAA’s behavioral analysis, external threat intelligence validation, and Endace’s definitive packet evidence gave us the confidence to take decisive action. We wrote up an Incident Report for the SOC managers, who authorized an immediate block on IP address 103.235.46[.]102 across our conference network infrastructure.
This incident perfectly illustrated the power of our integrated threat hunting stack. SAA’s automated analysis caught the initial suspicious URL, external threat intelligence provided crucial context about the infrastructure’s malicious history, and Endace delivered the packet-level proof we needed to confirm active threats and justify our response. In the high-stakes environment of conference security, where false positives can disrupt legitimate activities and false negatives can compromise attendee data, this multi-layered validation process has proved invaluable.
Check out the other blogs by my colleagues in the GovWare SOC.
About GovWare
GovWare Conference and Exhibition is the region’s premier cyber information and connectivity platform, offering multi-channel touchpoints to drive community intel sharing, training, and strategic collaborations.
A trusted nexus for over three decades, GovWare unites policymakers, tech innovators, and end-users across Asia and beyond, driving pertinent dialogues on the latest trends and critical information flow. It empowers growth and innovation through collective insights and partnerships.
Its success lies in the trust and support from the cybersecurity and broader cyber community that it has had the privilege to serve over the years, as well as organisational partners who share the same values and mission to enrich the cyber ecosystem.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media