Conference Wi-Fi networks are a chaotic environment where thousands of devices, each with their own history and configuration, converge and connect.
A common challenge is that attendees’ laptops and other devices, configured for ‘safer’ home or corporate environments, often connect to these conference networks with an implicit level of trust. This exposes sensitive secrets, which an opportunistic attacker can exploit.
The Security Operations Centre (SOC) at Cisco Live Melbourne is on the frontlines of this challenge. To effectively protect the network and educate attendees, our analysts need to rapidly understand the torrent of data flowing through our systems. We leverage powerful tools like Endace, which provides us with invaluable full packet capture …
Conference Wi-Fi networks are a chaotic environment where thousands of devices, each with their own history and configuration, converge and connect.
A common challenge is that attendees’ laptops and other devices, configured for ‘safer’ home or corporate environments, often connect to these conference networks with an implicit level of trust. This exposes sensitive secrets, which an opportunistic attacker can exploit.
The Security Operations Centre (SOC) at Cisco Live Melbourne is on the frontlines of this challenge. To effectively protect the network and educate attendees, our analysts need to rapidly understand the torrent of data flowing through our systems. We leverage powerful tools like Endace, which provides us with invaluable full packet capture capabilities, offering a deep, granular view of every byte traversing the network. However, raw packet data, while comprehensive, is an unorganized library. It’s with tools like Splunk Enterprise Security that we can truly extract value.
Rapid Orientation with Splunk’s field summary
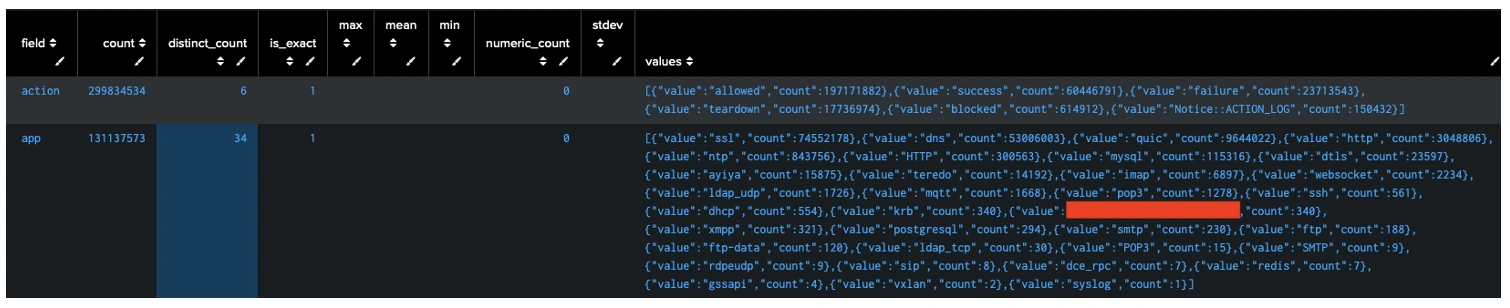
One of the simplest ways we accelerate understanding of new logs is by using Splunk Processing Language (SPL) commands designed to profile data quickly. The fieldsummary command is particularly effective: it analyzes a dataset for available fields, data types, cardinality, and null rates, giving analysts a fast and clear picture of the most valuable fields in a data set.
Typical flow: Ingest a new source, look for interesting fields and then run fieldsummary on them to reveal their most notable values, then pivot to targeted searches and dashboards tailored to the dataset’s most informative attributes.
Example SPL to quickly profile a new index:
index=se_network_endace ```contains all endace packet event logs```
| fieldsummary service path proto app action ```highlight fields that might contain interesting values```
Can you spot the protocols that would interest an attacker? While there are quite a few, this blog will focus on a handful.
Pivot: HTTP Authorization Headers and OAuth 2.0
With the data better understood, we can pivot to HTTP traffic that included Authorization headers. Modern web authentication heavily relies on TLS to protect secrets in transit, so it was very disappointing to see the volume of plain HTTP authentication.
Endace’s full packet capture was critical for precise reconstruction of sessions and headers for validation. Packet-level evidence confirmed that the observed Authorization scheme aligned with OAuth 2.0 patterns, commonly seen as Bearer and Refresh tokens. Anyone who obtains Bearer or Refresh tokens can access the resources those tokens grant until they expire or are revoked.
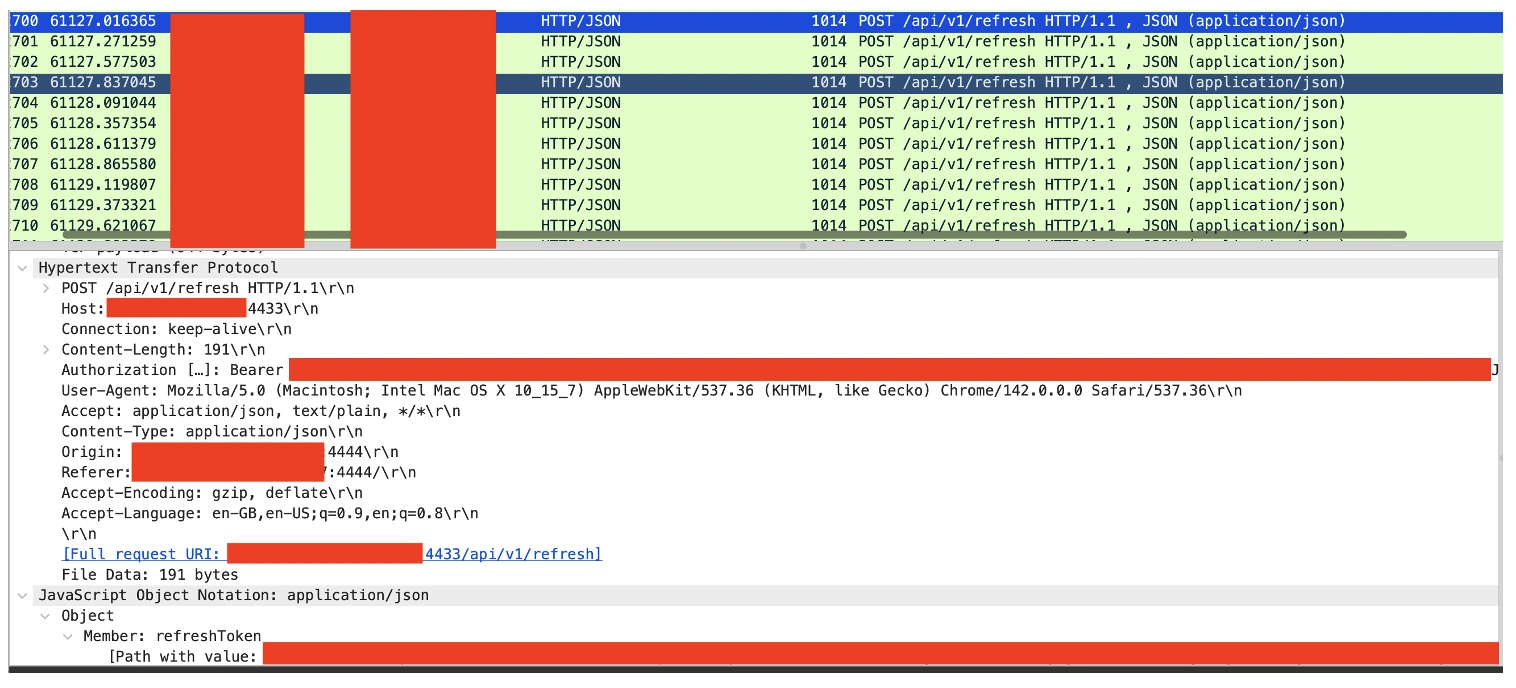
Why TLS is non-negotiable: OAuth 2.0 relies on Transport Layer Security (TLS) to protect secrets over the wire. Without strong, correctly configured TLS, credentials and tokens sent in headers are exposed in transit.
Pivot: Unusual Kerberos Activity on a Conference Network
Another notable observation was the presence of Kerberos activity on the guest network. Kerberos is a widely deployed authentication protocol typically found on internal enterprise networks (commonly within Active Directory domains). Kerberos uses a trusted Key Distribution Center (KDC) to issue time-bound tickets that prove identity securely without repeatedly sending passwords. Clients obtain a Ticket-Granting Ticket (TGT) from the KDC, then request service tickets to access individual services. These tickets are cryptographically protected and time-limited. In attackers’ hands, a Kerberos ticket can be leveraged to gain unauthorized access, move laterally across the network, or escalate privileges by impersonating legitimate users, making its detection on the network attractive for attackers.
Why Kerberos traffic matters to defenders:
- Secret Exposure: Kerberos on a transient, public network can indicate devices carrying corporate configurations into a conference environment, which may leak weakly encrypted secrets/passwords unintended for public networks.
- Public-facing KDC: Usage of Kerberos on the internet suggests a public-facing KDC (possibly also a Domain Controller) which is an attractive target for attackers.
Common attack surfaces to be aware of (high-level awareness for defenders):
- Ticket Replay and Impersonation Attempts: Reuse of valid tickets within their lifetime window to impersonate a legitimate user or service.
- Weak or Misconfigured Encryption: Use of deprecated ciphers or configurations that enable downgrade, interception, or decryption of tickets.
- Kerberoasting: An attacker with a valid ticket can request service tickets from the KDC which are encrypted with the service account password. If the password is weak, it can be decrypted.
- Time Skew and Validation Gaps: Unsynchronized clocks or lax validation can make replay and ticket acceptance more likely.
The Power of the Ecosystem
The Cisco Live SOC exemplified how a modern security ecosystem amplifies each component’s strengths while enabling deeper dives when warranted. Each platform contributed unique visibility and evidence, and each linked back to its native interfaces for expert-level analysis.
- Splunk: Rapid orientation with fieldsummary and fast pivots to hunts across diverse telemetry. Ideal for correlation, dashboards, and automation hooks.
- Endace: Packet-level truth on demand. PCAP confirmed protocol semantics, reconstructed headers, and validated behaviors that logs alone could not conclusively prove.
- Cisco XDR: Cross-signal correlation and incident management spanning Secure Firewall, Secure Access (DNS), Secure Network Analytics, and partner telemetry. Reduced swivel-chair analysis and tightened response loops.
- Secure Firewall and Secure Access: Inline enforcement and DNS-layer insight, turning detection into action while feeding back rich logs for investigation.
- Secure Network Analytics: NetFlow analytics to surface scanning, beaconing, and anomalous connection patterns at scale.
Together, the ecosystem shortened both detection and response times. Analysts could start with SPL summaries, escalate to correlation in XDR, and close the loop with packet proof in Endace.
Check out the other blogs by my colleagues in the Cisco Live Melbourne 2026 SOC.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media