Source: IM Imagery via Shutterstock
Manufacturers continued to be a top target — if not the top target — of financially motivated cyberattacks in 2025, with their sensitivity to operational disruptions and their shortage of expertise and well-designed protections causing issues for the business sector as a whole, experts say.
In 2025, half of manufacturers (51%) fell prey to ransomware and paid a ransom, with the average ransom costing $1 million and the average recovery cost (exclud…

Source: IM Imagery via Shutterstock
Manufacturers continued to be a top target — if not the top target — of financially motivated cyberattacks in 2025, with their sensitivity to operational disruptions and their shortage of expertise and well-designed protections causing issues for the business sector as a whole, experts say.
In 2025, half of manufacturers (51%) fell prey to ransomware and paid a ransom, with the average ransom costing $1 million and the average recovery cost (excluding the ransom) approaching $1.3 million, according to data that cybersecurity firm Sophos collected from more than 330 manufacturing organizations. In addition, for the first time in three years, exploited vulnerabilities were the most common root cause of compromises affecting the sector. In 2024, malicious emails were the top vector, while compromised credentials took the top slot in 2023.
While many factors contribute to the manufacturing sector’s appeal as a target, Rafe Pilling, director of threat intelligence for cybersecurity firm Sophos’ Counter Threat Unit, points to the top-three reasons manufacturers cited for breaches: A lack of security expertise and experts, previously unknown cybersecurity gaps, and a failure to adopt necessary protections.
"These organizations’ resilience depends both on their cybersecurity and technology maturity as well as their preparedness with having and regularly testing incident response plans to understand how to respond with speed," he says, adding that that makes the sector appealing to attackers. "Attackers know that any disruption can be incredibly costly, which creates pressure to resolve incidents quickly."
Related:CISA Warns of ‘Ongoing’ Brickstorm Backdoor Attacks
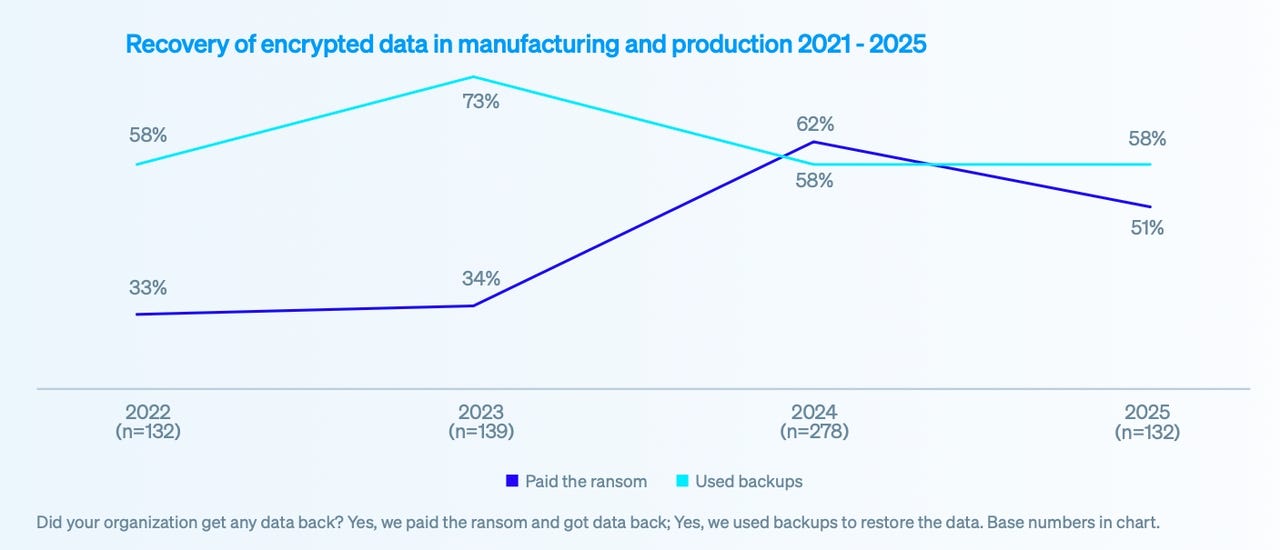
More than half of companies suffering a ransomware attack paid the ransom, while 58% used backups in 2025. Source: Sophos
Manufacturers have suffered notable cyberattacks this year. In early September, automaker Jaguar Land Rover suffered a ransomware attack and shut down production for the better part of a month, likely costing the company $1.7 billion to $2.4 billion. In late September, a similar attack shuttered operations at Japanese brewery and food giant Asahi Group Holdings, causing shortages of the company’s popular beers.
A Favored Target
At present, ransomware is one of the most significant threats. Manufacturers are vulnerable because operational downtime directly correlates to revenues, and so outages caused by ransomware are costly. In an analysis, Moscow-based cybersecurity firm Kaspersky Lab found that attacks on manufacturing firms outside of North America could have caused more than $18 billion in losses.
The estimates were based on detected ransomware attacks, which were prevented, against manufacturing organizations in each region, the average downtime experienced by publicly reported attacks, the size of their workforce, and the average hourly wage, says Dmitry Galov, head of the research for critical infrastructure services at Kaspersky’s Global Research and Analysis Team (GReAT).
Related:The Ransomware Holiday Bind: Burnout or Be Vulnerable
"When ransomware hits, production lines halt, triggering immediate revenue losses from an idle workforce and longer-term shortfalls from reduced output," he says. "Targeted ransomware is likely to remain a common threat to organizations, including manufacturing organizations."
Overall, manufacturers have been the most likely ransomware target for four year running, with 75% having a critical vulnerability with a Common Vulnerability Scoring System (CVSS) score of 8.0 or higher, according to cybersecurity vendor Black Kite. Among businesses that use operational technology, manufacturers are the top target, with 42% of attacks targeting the industrial sector, according to Trellix, a threat detection and response vendor.
"In 2026, 27, 28 — if the geopolitical situation keeps going downward, and production and military investments continue to go up, definitely the trend [in attacks] will continue," says Mo Cashman, field chief technology officer for Europe, the Middle East and Africa at Trellix. "Transportation and energy are also the other two big industries [whose resilience] we have to be worried about, and which I think there are equally vulnerable in terms of their value."
Related:AI Bolsters Python Variant of Brazilian WhatsApp Attacks
AI Brings New Opportunities, New Risks
Manufacturers and their automation suppliers are moving quickly to adopt AI. In November, for example, manufacturing giant Foxconn and Alphabet’s AI robotics company Intrinsic announced a joint venture to "make the intelligent factory of the future a reality." The same month, Munich-based Agile Robots acquired Thyssenkrupp Automation Engineering aiming to develop physical AI — or intelligent robotics — to help drive the next industrial shift toward smart factories, the companies said.
Optimizing production, adaptive maintenance, and other capabilities can all be unlocked with enough data and the right AI services and agents, but the increasing automation also poses security issues. On Dec. 3, the US Cybersecurity and Infrastructure Security Agency (CISA) released a best practices document for manufacturers and other firms who aim to integrate AI into their operational technology environments.
Because so much of the operational technology is now automated, there is an increasing amount of data kept by manufacturers that is valuable for training AI capabilities, says Sophos’s Pilling.
"From a cybersecurity perspective as the boundaries between IT and OT environments have been eroded, we’ve seen increased numbers of attacks crossing that boundary and impacting manufacturing operations," Pilling says. "Adding AI into the technology stack adds increased complexity and attack surface but is also inevitable."
About the Author
Veteran technology journalist of more than 20 years. Former research engineer. Written for more than two dozen publications, including CNET News.com, Dark Reading, MIT’s Technology Review, Popular Science, and Wired News. Five awards for journalism, including Best Deadline Journalism (Online) in 2003 for coverage of the Blaster worm. Crunches numbers on various trends using Python and R. Recent reports include analyses of the shortage in cybersecurity workers and annual vulnerability trends.