NCSC warns prompt injection threats might be forever, Apple and Google issue new spyware warnings, Apache Tika critical flaw allows XXE injection attacks, Japanese high school student accused of using ChatGPT to attack internet cafe chain, US issues $10m reward for Iranian hackers, much more
08 Dec 2025 — 10 min read
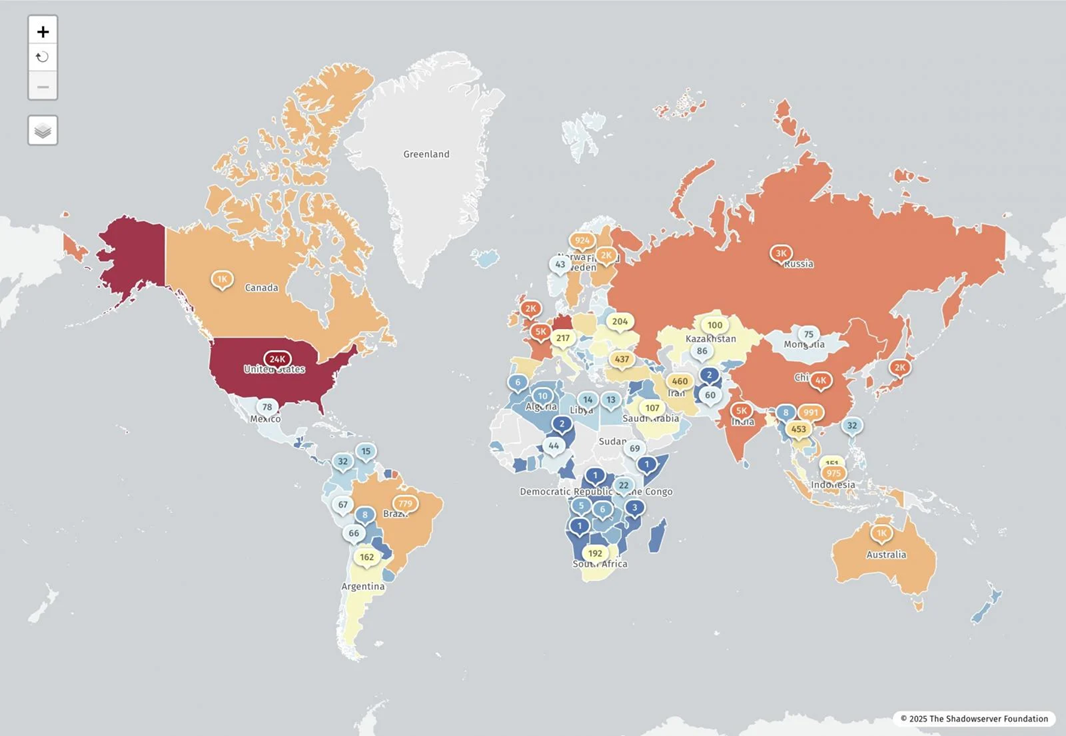
 Geographic distribution of IP addresses vulnerable to React2Shell. Source: ShadowServer
Geographic distribution of IP addresses vulnerable to React2Shell. Source: ShadowServer
**’Tis the season to be generous. Please support Metacurity in our mission to end infosec new…
NCSC warns prompt injection threats might be forever, Apple and Google issue new spyware warnings, Apache Tika critical flaw allows XXE injection attacks, Japanese high school student accused of using ChatGPT to attack internet cafe chain, US issues $10m reward for Iranian hackers, much more
08 Dec 2025 — 10 min read

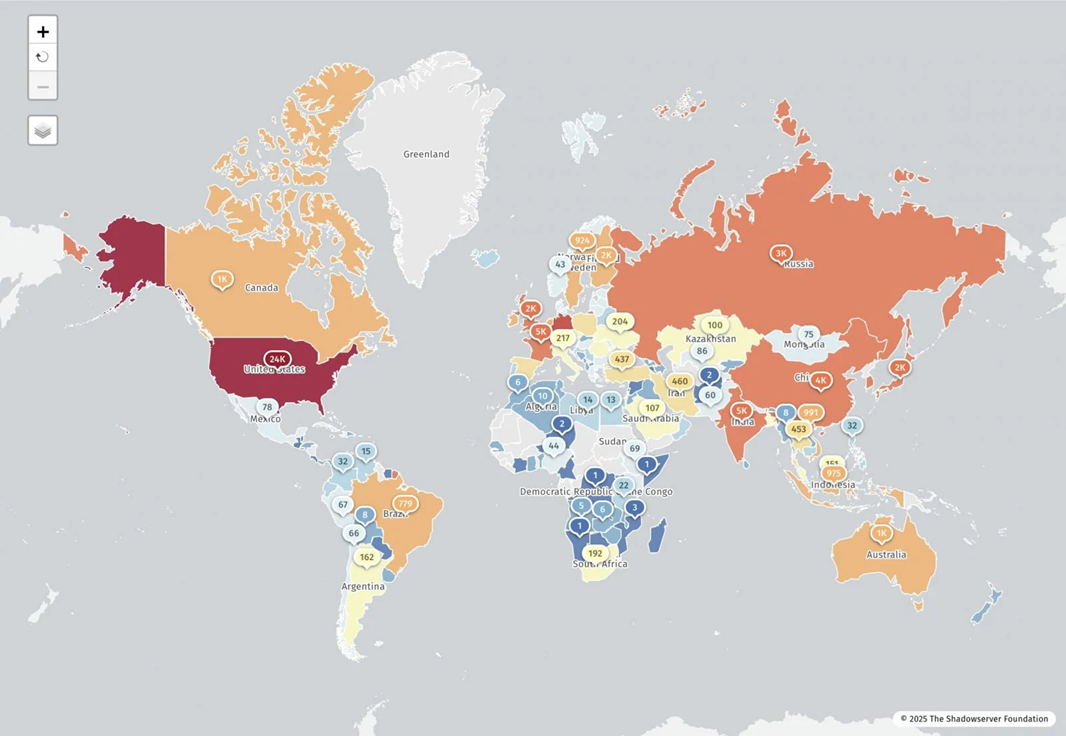
 Geographic distribution of IP addresses vulnerable to React2Shell. Source: ShadowServer
Geographic distribution of IP addresses vulnerable to React2Shell. Source: ShadowServer
’Tis the season to be generous. Please support Metacurity in our mission to end infosec news overload.
Metacurity is a pure labor of love and is the only daily newsletter that delivers the critical infosec developments you need to know, scanned from thousands of sources and smartly summarized.
But to continue delivering our daily updates, we need your support. Please consider upgrading to an annual paid subscription today.
If you can’t upgrade to a paid subscription today, please consider donating what you can.
Security researcher Lachlan Davidson discovered and reported to React a maximum severity vulnerability, dubbed ‘React2Shell,’ in the React Server Components (RSC) ‘Flight’ protocol, which allows remote code execution without authentication in React and Next.js applications.
Over 77,000 Internet-exposed IP addresses are vulnerable to the critical React2Shell remote code execution flaw (CVE-2025-55182), with researchers now confirming that attackers have already compromised over 30 organizations across multiple sectors.
The security issue stems from insecure deserialization. It received a severity score of 10/10 and has been assigned the identifiers CVE-2025-55182 for React and CVE-2025-66478 (CVE rejected in the National Vulnerability Database) for Next.js.
Davidson discovered the flaw and reported it to React on November 29. He found that an attacker could achieve remote code execution (RCE) by sending a specially crafted HTTP request to React Server Function endpoints.
Researchers at Wiz cloud security platform warn that the vulnerability is easy to exploit and exists in the default configuration of the affected packages.
According to React, the vulnerability is present in versions 19.0, 19.1.0, 19.1.1, and 19.2.0. Next.js is impacted in experimental canary releases starting with 14.3.0-canary.77, and all releases of the 15.x and 16.x branches below the patched versions.
The flaw exists in the ‘react-server’ package used by React Server Components (RSC), but Next.js inherits it through its implementation of the RSC "Flight" protocol.
Wiz researchers say that 39% of all cloud environments where they have visibility contain instances of Next.js or React running versions vulnerable to CVE-2025-55182, CVE-2025-66478, or both.
The same vulnerability likely exists in other libraries that implement React Server, including the Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, and Waku.
Davidson created a React2Shell website, where he will publish technical details. The researcher is also warning that there are proof-of-concept (PoCs) exploits that are not genuine.
Developers are strongly advised to apply the fixes available in React versions 19.0.1, 19.1.2, and 19.2.1, and Next.js versions 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, and 16.0.7. (Bill Toulas / Bleeping Computer and Lawrence Abrams / Bleeping Computer)
***Related: **React, React2Shell, Security Affairs, AWS, Wiz, GreyNoise, The Record, The Register, Security Week, Bleeping Computer, Industrial Cyber, Cyber Security News, Techzine Europe, *SQ Magazine
The UK’s NCSC is warning that language models may never be fully protected from “prompt injection,” a growing type of cyber threat that manipulates AI systems into ignoring their original instructions.
Attackers have used prompt injection to discover the hidden instructions for Microsoft’s New Bing search engine, or to steal secrets through GitHub’s Copilot, and — at least in theory — to trick AI evaluations of job applicant résumés.
The NCSC’s technical director for platforms research, David C, warned that the trend of embedding generative AI into digital systems globally could trigger a wave of security breaches worldwide. NCSC, as a part of the cyber and signals intelligence agency GCHQ, does not disclose most staff’s surnames.
“On the face of it, prompt injection can initially feel similar to that well known class of application vulnerability, ‘SQL injection’,” he wrote. “However, there are crucial differences that if not considered can severely undermine mitigations.”
He said many security professionals mistakenly assume prompt injection resembles SQL injection, a comparison he argued is “dangerous” because the threats require different approaches. SQL injection allows attackers to send malicious instructions to a database by using a field to input data. (Alexander Martin / The Record)
*Related: NCSC, Digit, *CrowdStrike
Apple and Google sent a new round of cyber threat notifications to users around the world, the companies said this week, announcing their latest effort to insulate customers against surveillance threats.
Apple and the Alphabet-owned Google are two of several tech companies that regularly issue warnings to users when they determine state-backed hackers may have targeted them.
Apple said the warnings were issued on Dec. 2 but gave few further details about the alleged hacking activity and did not address questions about the number of users targeted or say who was thought to be conducting the surveillance. Apple said that "to date we have notified users in over 150 countries in total."
Apple’s statement follows Google’s Dec. 3 announcement that it was warning all known users targeted using Intellexa spyware, which it said spanned "several hundred accounts across various countries, including Pakistan, Kazakhstan, Angola, Egypt, Uzbekistan, Saudi Arabia, and Tajikistan."
Google said in its announcement that Intellexa, a cyber intelligence company that the US government sanctioned, was "evading restrictions and thriving." (Raphael Satter / Reuters)
*Related: Google, Tech Republic, ET Insights, The Cyber Express, Greek City Times, Times of India, Tech in Asia, The420, *Middle East Monitor
A critical-severity vulnerability in the Apache Tika open source analysis toolkit could allow attackers to perform XML External Entity (XXE) injection attacks.
Apache Tika functions as a universal parser capable of extracting information from virtually all types of files, making it a core part of indexing and analysis tools.
The critical issue, tracked as CVE-2025-66516 (CVSS score of 10/10), impacts the tika-core, tika-pdf-module, and tika-parsers modules of Apache Tika.
Attackers can exploit the flaw via crafted XFA files placed inside PDF files, on all platforms.
Successful exploitation of XXE injection weaknesses could typically lead to information leaks, SSRF attacks, denial-of-service (DoS), or remote code execution (RCE).
The vulnerability poses a major risk, given the essential role Apache Tika has within search engines, content management systems, and data analysis tools.
The newly disclosed Apache Tika vulnerability was patched in tika-core version 3.2.2, tika-parser-pdf-module version 3.2.2, and tika-parsers version 2.0.0.
The affected modules are used as dependencies in other packages. Users are advised to apply the patches as soon as possible. (Ionut Arghire / Security Week)
*Related: Apache, The Register, Security Affairs, *GBHackers
A high school student from Osaka Prefecture, western Japan, has been arrested for carrying out cyberattacks on an internet cafe operator, allegedly assisted by ChatGPT.
More than 7 million pieces of personal data were reportedly leaked.
Tokyo police say an official app managed by the operator of the Kaikatsu Club internet cafe chain came under cyberattack in January.
Police arrested the 17-year-old, who faces charges of unauthorized computer access and fraudulent obstruction of business.
The suspect reportedly began teaching himself programming skills when he was in elementary school and won an award in a cybersecurity contest.
He is believed to have created the malware on his own.
The company noticed the cyberattack and took defensive action.
The suspect then allegedly asked ChatGPT for ways to slip through the company’s security system and used the information to alter his program. The malware carried out more than 7.24 million cyberattacks.
The company was forced to suspend some functions of its app. (NHK World Japan)
*Related: The Japan Times, JiJi Press, The Japan News, *The Mainichi
The US Department of State’s Rewards for Justice Program is offering up to a $10 million reward for information on Fatemeh Sedighian Kashi and Mohammad Bagher Shirinkar, a pair of Iranian hackers linked to the Islamic Revolutionary Guard Corps (IRGC).
The US Department of Defense itself reported this in a note on X, stating that the two Iranian operators work for Shahid Shushtari, a cyber organization linked to the IRGC-CEC.
According to the US government, Shahid Shushtari members "have caused significant financial damage and disruption to US companies and government agencies through cyber-based information and information operations.
These campaigns have targeted multiple critical infrastructure sectors, including news, shipping, travel, energy, finance, and telecommunications in the United States, Europe, and the Middle East." According to the information collected, Shirinkar oversees the group, while Kashi is a longtime employee of Shahid Shushtari who works closely with Shirinkar in planning and conducting cyber operations. (Agenzia Nova)
*Related: Rewards for Justice, Iran International, Iran Focus, *The Cyber Express
Portugal has modified its cybercrime law to establish a legal safe harbor for good-faith security research and to make hacking non-punishable under certain strict conditions.
First spotted by Daniel Cuthbert, a new provision in Portugal’s Article 8.o-A, titled "Acts not punishable due to public interest in cybersecurity," provides a legal exemption for actions that previously were classified as illegal system access or illegal data interception.
The exemption only applies when security researchers act for the purpose of identifying vulnerabilities and contributing to cybersecurity. Eight key conditions must be met to be safe from criminal liability.
The new article clearly defines the limits of security research, and at the same time provides legal protection for well-intended hackers. (Bill Toulas / Bleeping Computer)
*Related: *Databreaches.net
New research from Israeli cybersecurity firm Malanta suggests Indonesia’s sprawling gambling ecosystem, long dismissed as routine cybercrime, exhibits the scale, automation, and operational maturity typically associated with state-sponsored threat actors.
Malanta uncovered a unified infrastructure active since at least 2011, revealing more than 328,000 domains, 236,000 gambling sites, 1,400 hijacked subdomains, and thousands of malicious Android applications — an ecosystem large enough to rival established APT groups.
The operation also includes stolen credentials, reverse proxies buried inside government and enterprise environments, and over 500 impersonation domains mimicking major brands.
This indicates a threat actor capable of silently staging large-scale operations years before launching full attacks.
The infrastructure’s reach into Western government systems and cloud environments elevates its national security and supply chain impact.
Malanta published the full list of attacker-owned domains on its GitHub so defenders can take immediate action. (Ken Underhill / eSecurityPlanet)
*Related: Malanta, Cyber Security News, GBHackers, *GitHub
Internal documents and insider communications obtained by CDG News reveal that 700Credit, one of the auto industry’s largest credit reporting and identity verification providers, experienced a data breach on or around October 25, 2025.
Consumer names, addresses, and Social Security numbers from auto financing applications submitted between May and October 2025 were compromised, according to a letter sent to its dealer partners.
Dark web monitoring service databreach.io first flagged the breach in mid-November after spotting threat actors trying to sell stolen data online.
The listing claimed the database contained over 8 million records and that negotiations between attackers and the company had broken down. However, managing director Ken Hill told CDG News that only 5.6 million records were implicated. (Anna del Villar / CarDealershipGuy)
*Related: Auto News, CBT News, Tech Republic, *RVPro
Korean retailer Coupang, which caused a data breach affecting 33.7 million customers, only subscribed to the minimum coverage amount for the statutory mandatory ‘personal information leakage compensation insurance.’
According to the non-life insurance industry on the 8th, Coupang is currently enrolled in Meritz Fire & Marine Insurance’s personal information leakage compensation liability insurance with a coverage limit of 1 billion Korean won.
This level of coverage means the maximum insurance payout Coupang can access for compensating customers affected by the recent hacking incident is only 1 billion Korean won, or around $682,000. It is known that Coupang has not yet reported the insurance incident to Meritz Fire & Marine Insurance.
The current Personal Information Protection Act mandates that companies with annual sales of over 1 billion Korean won and managing data of at least 10,000 individuals must subscribe to personal information leakage compensation insurance. However, the minimum required coverage based on company size ranges from 50 million to 1 billion Korean won, which is considered very low.
Meanwhile, the government unveiled plans to toughen the management and screening process for the state-certified information security system amid growing personal data breaches at authorized companies, such as Coupang.
The Personal Information Protection Commission and the Ministry of Science and ICT discussed the measures during an interagency meeting earlier in the day, as public distrust has grown over data security protection following the massive personal data breach at e-commerce giant Coupang.
Coupang recently disclosed that personal information belonging to over 33 million customers had been leaked and remained undetected for months, heightening privacy concerns in one of the world’s most advanced information technology nations. (Kang Woo-ryang / The Chosun Daily, Yonhap News Agency, Yonhap News Agency)
*Related: Insurance Asia News, *KoreaJoongAng Daily
Police investigating the KT Corp. payment breach and micropayment scam said they have identified the mastermind behind the crime, known as a Chinese national of Korean ethnicity.
The Gyeonggi Nambu Provincial Police Agency said it has asked Interpol for cooperation in a manhunt for the Chinese suspect currently residing in China.
He is known to have orchestrated the hacking of KT mobile users in the Seoul metropolitan area between August and September to make illegal small transactions, such as purchasing gift certificates. So far, about 220 victims have reported combined damage worth 140 million won ($95,300).
He is accused of having instructed another Chinese national to use an illegal portable base station to breach the phones of KT users. The co-conspirator arrested in mid-September told police that he took part in the scheme in exchange for 5 million won from the mastermind.
Police have so far apprehended 13 people, mostly South Korean nationals, in connection with the KT payment breach case and put five of them under arrest. (Yonhap News)
*Related: Yonhap News, The Chosun Daily, *Donga
Agentic browsers are too risky for most organizations to use, according to analyst firm Gartner.
The firm offered that advice in a new advisory titled “Cybersecurity Must Block AI Browsers for Now,” in which research VP Dennis Xu, senior director analyst Evgeny Mirolyubov, and VP analyst John Watts observe “Default AI browser settings prioritize user experience over security.”
The analysts’ definition of an AI browser encompasses tools like Perplexity’s Comet and OpenAI’s ChatGPT Atlas that include two elements: An “AI sidebar” that offers users the chance to summarize, search, translate, and interact with web content using AI services provided by the browser’s developer and an agentic transaction capability that allows the browser to autonomously navigate, interact with, and complete tasks on websites, especially within authenticated web sessions.
Gartner’s fears about the agentic capabilities of AI browser relate to their susceptibility to “indirect prompt-injection-induced rogue agent actions, inaccurate reasoning-driven erroneous agent actions, and further loss and abuse of credentials if the AI browser is deceived into autonomously navigating to a phishing website.”
The authors also suggest that employees “might be tempted to use AI browsers and automate certain tasks that are mandatory, repetitive, and less interesting” and imagine some instructing an AI browser to complete their mandatory cybersecurity training sessions.
Another scenario they consider is exposing agentic browsers to internal procurement tools, then watching LLMs make mistakes that cause organizations to buy things they don’t want or need. (Simon Sharwood / The Register)
***Related: **Gartner, r/technology, *Techzine
Best Thing of the Day: Another Malicious App Rejected by Google
A Customs and Border Protection (CBP) app that lets local cops use facial recognition to hunt immigrants on behalf of the federal government has been removed from the Google Play Store.
Worst Thing of the Day: Hacking Starts as Child’s Play?
Children as young as seven are being referred to Britain’s national cybercrime intervention program, Cyber Choices.
Closing Thought
