
Source: Dragos Condrea via Alamy Stock Photo
China-linked advanced persistent threat (APT) groups are wreaking havoc in Asia with new cyber weaponry, targeting Chinese gambling sites and government entities in the region.
The Asia-Pacific (APAC) region is among the world’s busiest in terms of cyberattacks, accounting for just over half of all APT activity in the world…

Source: Dragos Condrea via Alamy Stock Photo
China-linked advanced persistent threat (APT) groups are wreaking havoc in Asia with new cyber weaponry, targeting Chinese gambling sites and government entities in the region.
The Asia-Pacific (APAC) region is among the world’s busiest in terms of cyberattacks, accounting for just over half of all APT activity in the world, according to one study. It helps that a plurality of people in the whole world live there (so there’s a lot going on), and that countries like Japan, China, and South Korea have fat economies and geopolitical influence. North Korea’s state crowdfunding has something to do with it, as do internecine conflicts in South Asia. By far the biggest reason for this, though, is China. Chinese state APTs are some of the best in the world, using and often inventing advanced malware, and tactics, techniques, and procedures (TTPs). They’re highly active, and often rather difficult to pin down, since they share their resources and knowhow within loosely understood clusters and networks. Those networks sometimes even extend beyond state-aligned organizations, involving private institutions and even criminal outfits.
Related:Coyote, Maverick Banking Trojans Run Rampant in Brazil
For instance, Trend Micro has been tracking two threat actors using the same "sophisticated" command-and-control (C2) tool, dubbed "PeckBirdy," since 2023. In the first campaign, a financially motivated cybercrime group has used PeckBirdy to create watering holes on Chinese gambling websites. In the second, an espionage-focused group has been fittingly more ambitious — it more creatively used PeckBirdy to deliver malware and steal credentials from some private organizations and mostly government-affiliated targets around Asia.
Attacks Hit Chinese Gambling Industry and Asian Governments
In 2023, a number of Chinese gambling sites had been surreptitiously infected with the PeckBirdy C2 framework. Whenever a new user came to the site, they’d be visited by a malicious script, loading PeckBirdy into their browser. PeckBirdy would show them a fake Google Chrome software update page, and if they bought it and downloaded the fake update, their jackpot would be advanced, modular backdoors: "Holodonut" and "MKDoor." The same server that hosted all this malware also hosted additional PeckBirdy scripts: one for establishing a reverse shell, and another for exploiting a vulnerability in Google Chrome (CVE-2020-16040).
PeckBirdy might be viewed as one byproduct of the rising browser threats in Asia. The vast majority of workplace activity occurs in browsers, which has invited huge upticks in attacks against this space. In 2024, for example, Akamai Technologies tracked 22 billion more browser-based cyberattacks in APAC than it had in 2023.
Related:WorldLeaks Extortion Group Claims It Stole 1.4TB of Nike Data
A pile of evidence suggests that this campaign was carried out by a Chinese APT, but exactly which is unclear. Chinese threat actors are notorious for sharing tools, techniques, and infrastructure. Trend Micro found that this one — which it currently tracks as Shadow-Void-044 — used a C2 domain previously used by UNC3569. A Cobalt Strike sample on one of its servers was signed with a stolen certificate also spotted in a Bronze University campaign. And they linked one of its backdoors to a backdoor developed by a group called "TheWizards," not to be confused with the equally maligned basketball team.
A second, separate threat actor has also been using PeckBirdy since at least July 2024. With low confidence, Trend Micro’s report linked the group it labeled Shadow-Earth-045 to the one it tracks as Earth Baxia. This campaign was more diverse in its methods, and its targeting, involving both Asian private organizations and government entities. Chinese APTs habitually perform cyberespionage against government agencies in the APAC region and beyond.
Trend Micro tells Dark Reading, "These two campaigns remind us that the boundary between cybercrime and cyberespionage is increasingly blurred. One tool used in different [kinds of] attacks is [becoming] more and more popular."
Related:DPRK’s Konni Targets Blockchain Developers With AI-Generated Backdoor
The company adds that the threat actors "are likely efficient, stealthy contractors who use shared tools to handle day-to-day business. Compared to past cases, their working style is a little similar to APT41," though APT41 isn’t specifically linked to either group.
Shapeshifting PeckBirdy C2
In one instance, Shadow-Earth-045 used the Mshta Windows utility to run PeckBirdy and establish a remote access channel into a private organization. In another case, it created a .NET executable and triggered PeckBirdy using the legacy Windows component "ScriptControl." PeckBirdy can also run in a NodeJS, Windows Script Host (WScript), or classic Active Server Pages (ASP) environment.
"The malware allows threat actors to change their attack vectors based on their target’s environment and their needs (not all at once)," Trend Micro points out.
The way it’s deployed also affects what it can do for you. In one context, it might be limited by a browser’s sandbox environment. In another, like with Mshta, it can execute actions directly on a victim’s machine. The following table outlines what it can do for attackers in each case:
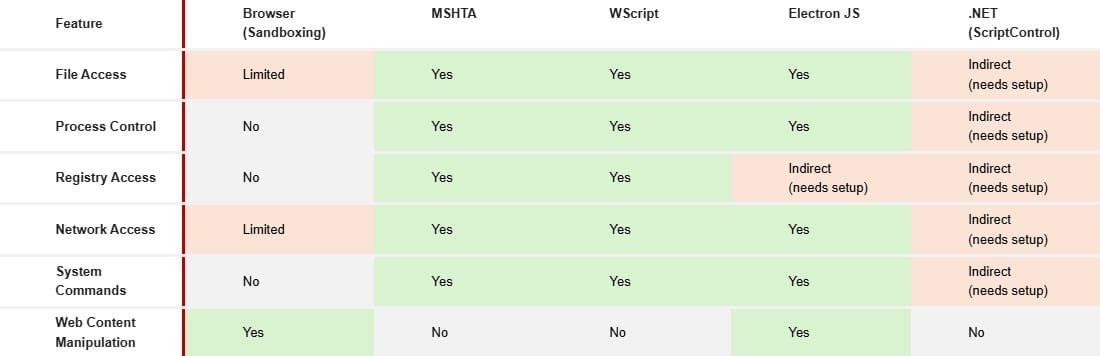
Source: Trend Micro
It all works because PeckBirdy is written in an old, generic scripting language — JScript — which allows it to form-fit different environments using different living-off-the-land binaries (LOLbins). When it first executes, it searches for specific clues to figure out which kind of environment it’s running in — "window" in a browser, "process" in NodeJS, etc.
"The attackers can use the exact same tool to infect a casual visitor on a gambling website and a government employee at their desk," Trend Micro says. "They spend less time writing code and more time stealing data, all while staying quiet enough to avoid getting kicked out of the network."
About the Author
Nate Nelson is a journalist and scriptwriter. He writes for "Darknet Diaries" — the most popular podcast in cybersecurity — and co-created the former Top 20 tech podcast "Malicious Life." Before joining Dark Reading, he was a reporter at Threatpost.