On September 11, 2025, the Federal Trade Commission started an inquiry into seven major companies: Alphabet, CharacterAI, Instagram, Meta, OpenAI, Snapchat, and xAI. The investigation focuses on three important areas: risks to child safety, misleading data collection practices, and emotional manipulation of young users.

This isn’t a regulatory theater. Multiple companies face lawsuits from families whose children died by suicide after chatbots allegedly encouraged self-harm. For developers, the message is clear: build it wrong, and you’re looking at massive fines, platform bans, or worse; you become a contributor to genuine harm.
In this tutorial, we will build a production-grade…
On September 11, 2025, the Federal Trade Commission started an inquiry into seven major companies: Alphabet, CharacterAI, Instagram, Meta, OpenAI, Snapchat, and xAI. The investigation focuses on three important areas: risks to child safety, misleading data collection practices, and emotional manipulation of young users.

This isn’t a regulatory theater. Multiple companies face lawsuits from families whose children died by suicide after chatbots allegedly encouraged self-harm. For developers, the message is clear: build it wrong, and you’re looking at massive fines, platform bans, or worse; you become a contributor to genuine harm.
In this tutorial, we will build a production-grade, compliant chatbot system from the ground up. You’ll learn how to implement FTC-mandated safeguards. This includes strong age verification, real-time safety monitoring, transparent data handling, and limits on engagement to prevent addictive patterns.
Let’s get started.
🚀 Sign up for The Replay newsletter
The Replay is a weekly newsletter for dev and engineering leaders.
Delivered once a week, it’s your curated guide to the most important conversations around frontend dev, emerging AI tools, and the state of modern software.
Prerequisites
Before starting, ensure you have:
- Experience with React for frontend and Node.js for backend development
- Node.js 18+, npm or yarn, and a code editor
- MongoDB and Redis are installed locally or accessible through cloud services
- Accounts for age verification services like Yoti, or Jumio (we’ll use mock implementations for the demonstration, which you can replace with real providers)
- A basic understanding of COPPA (Children’s Online Privacy Protection Act) and FTC guidelines for AI applications
The complete code for this tutorial is available on GitHub on the master branch, and you can follow along step-by-step as we build each component.
What is the FTC’s AI chatbot inquiry?
The FTC’s Section 6(b) inquiry examines how these seven companies assess, test, and monitor the potential negative impacts of companion chatbots on children and teens. Unlike traditional software, AI chatbots simulate human-like emotional connections, effectively mimicking characteristics to prompt users (especially young people) to trust and form relationships with what they perceive as a confidant.
The inquiry seeks detailed information in several key areas: how companies generate revenue from user interactions, how they process inputs and produce outputs, the criteria for designing chatbot personalities, and the steps they take to protect minors from psychological harm.
This builds on the FTC’s 2024 guidance framework. The earlier guidance outlined five critical “dont’s” for AI chatbots: don’t misrepresent what the AI is or what it does, don’t offer services without mitigating harmful outputs, don’t exploit emotional relationships for commercial gain, don’t make unsubstantiated claims, and don’t use automated tools to mislead people. The 2025 inquiry builds on these principles, specifically targeting companion bots and their unique risks to vulnerable users.
For developers, this means clear technical requirements. You need verifiable age gates, regular safety checks, clear UI disclosures, traceable data flows, and ways to prevent manipulative engagement patterns. These are not optional features. They’re table stakes for operating legally in this space.
Why do traditional chatbot designs fall short for compliance?
Most chatbot implementations prioritize user experience and engagement metrics above all else. Many chatbot designs still overlook some basic safety steps, such as:
- A simple “Are you 13?” checkbox doesn’t cut it anymore. The FTC expects real age verification and access controls that are difficult to bypass – not flimsy self-reporting
- Relying on user complaints is already too late. You need real-time monitoring that flags harmful or risky content before it ever reaches users, especially minors discussing self-harm, substance use, or similar crises
- When regulators ask questions, you should be able to show exactly what data you collected, from whom, how it was processed, and how it was protected. Yet most chatbots still treat logging as an afterthought
- If your revenue model depends on keeping users chatting longer, you’re walking into a compliance minefield. The FTC explicitly warns against monetizing the emotional trust chatbots build with users
The solution isn’t about adding compliance features later. You need to create structured pipelines for verification, evaluation, and monitoring in your architecture from the start.
Building the compliant chatbot
Now that you know what the FTC inquiry expects from AI chatbots, let’s move on to learning how to use these in your existing or new chatbot projects.
Project setup
Before we build the compliance features, let’s set up our development environment. First, clone the starter project for this tutorial by running the command:
git clone https://github.com/Claradev32/compliant-chatbot
The project you just cloned contains the basic folder structure and dependencies for the application. This will enable us to focus on building out the main compliance features.
Then, change the directory into the project folder and install the project dependencies by running the following command:
cd compliant-chatbot && npm install
Now, create a .env file in the backend directory and add the following configurations:
PORT=3001
NODE_ENV=development
MONGODB_URI=your_mongodb_uri_here
OPENAI_API_KEY=your_openai_api_key_here
SESSION_SECRET=your_random_secret_key_here
DAILY_MESSAGE_LIMIT=50
DAILY_SESSION_LIMIT=6
MAX_SESSION_DURATION=3600
DATA_RETENTION_DAYS=90
Add age gating with verifiable checks
Age verification is your first line of defense. The FTC requires companies to implement meaningful age restrictions to limit children’s access to potentially harmful content, and that means going beyond simple checkboxes.
Let’s create a new React component for age verification in components/AgeGate.jsx:
import { useState } from "react";
export default function AgeGate({ onVerified }) {
const [verifying, setVerifying] = useState(false);
const [error, setError] = useState(null);
const handleVerification = async (e) => {
e.preventDefault();
setVerifying(true);
setError(null);
try {
const response = await fetch("/api/verify-age", {
method: "POST",
headers: { "Content-Type": "application/json" },
body: JSON.stringify({
timestamp: Date.now(),
}),
});
const data = await response.json();
if (data.verified) {
sessionStorage.setItem("ageVerified", "true");
sessionStorage.setItem("userId", data.userId);
onVerified({ userId: data.userId });
} else {
setError(data.message || "Age verification failed. You must be 13 or older to use this service.");
}
} catch (err) {
setError("Verification service unavailable. Please try again later.");
} finally {
setVerifying(false);
}
};
return (
<div className="fixed inset-0 bg-gray-900 bg-opacity-90 flex items-center justify-center z-50">
<div className="bg-white rounded-lg p-8 max-w-md w-full mx-4">
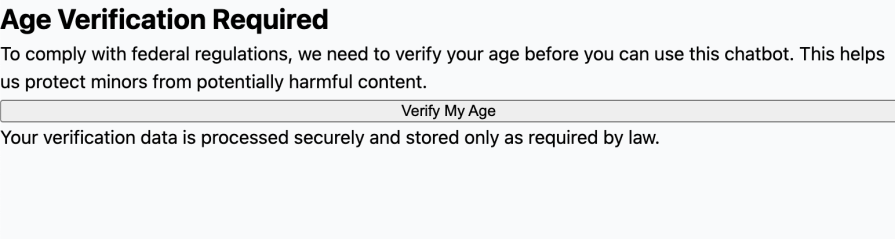
<h2 className="text-2xl font-bold mb-4">Age Verification Required</h2>
<p className="text-gray-600 mb-6">
To comply with federal regulations, we need to verify your age before
you can use this chatbot. This helps us protect minors from
potentially harmful content.
</p>
{error && (
<div className="bg-red-50 border border-red-200 rounded p-4 mb-4">
<p className="text-red-800 text-sm">{error}</p>
</div>
)}
<button
onClick={handleVerification}
disabled={verifying}
className="w-full bg-blue-600 text-white py-3 rounded-lg hover:bg-blue-700 disabled:opacity-50"
>
{verifying ? "Verifying..." : "Verify My Age"}
</button>
<p className="text-xs text-gray-500 mt-4">
Your verification data is processed securely and stored only as
required by law.
</p>
</div>
</div>
);
}
This component uses the useState Hook to manage the verification state, tracking whether verification is in progress(verifying) and capturing any errors that occur. The handleVerification function sends a POST request to the /api/verify-ageendpoint along with a timestamp. When verification succeeds, the user’s ID is stored in sessionStorage, and the parent component is notified through the onVerified callback. This approach allows the verification state to persist across the user’s session while upholding data minimization principles and ensuring regulatory compliance.
Building the backend verification endpoint
Now let’s implement the server-side verification logic inserver/routes/ageVerification.js:
const express = require('express');
const { logAuditEvent } = require('../services/auditLogger');
const router = express.Router();
router.post('/verify-age', async (req, res) => {
try {
// Random verification for demo (50/50 chance)
const verified = Math.random() > 0.5;
const userId = `user_${Date.now()}_${Math.random().toString(36).substr(2, 9)}`;
try {
await logAuditEvent({
eventType: 'AGE_VERIFICATION',
userId,
verified,
timestamp: new Date(),
ipAddress: req.ip,
metadata: {
provider: 'demo_random',
sessionId: req.body.timestamp
}
});
} catch (auditError) {
// Continue without audit if it fails
}
if (verified) {
res.cookie('verified', userId, {
httpOnly: true,
secure: process.env.NODE_ENV === 'production',
maxAge: 24 * 60 * 60 * 1000
});
}
res.json({
verified,
userId: verified ? userId : null,
message: verified ? 'Age verification successful' : 'Age verification failed - you must be 13 or older to use this service'
});
} catch (error) {
res.status(500).json({ error: 'Verification service temporarily unavailable' });
}
});
module.exports = router;
Here, the Express router processes POST requests to /verify-age. For demonstration purposes, it randomly approves or denies verification, but in production, this endpoint would integrate with a third-party age verification provider to confirm a user’s age before granting access to the chatbot. Each verification attempt is logged using logAuditEvent, which records the user ID, verification result, IP address, and timestamp. When verification succeeds, the server sets an httpOnly cookie – shielding it from client-side JavaScript and adding an extra layer of security. The maxAge of 24 hours ensures that users must reverify once per day:
Creating the audit logging service
To maintain compliance records, we need a robust audit logging system in server/services/auditLogger.js:
const { MongoClient } = require('mongodb');
let client;
let db;
let auditLog;
async function initializeDatabase() {
if (!client) {
client = new MongoClient(process.env.MONGODB_URI || 'mongodb://localhost:27017');
await client.connect();
db = client.db('chatbot_compliance');
auditLog = db.collection('audit_events');
}
}
async function logAuditEvent(event) {
try {
await initializeDatabase();
const record = {
...event,
_id: `audit_${Date.now()}_${Math.random().toString(36).substr(2, 9)}`,
createdAt: new Date()
};
await auditLog.insertOne(record);
return record._id;
} catch (error) {
console.error('Audit logging failed (continuing without audit):', error.message);
return null;
}
}
module.exports = { logAuditEvent };
This service connects to MongoDB using the MongoClient class. The initializeDatabase function follows a singleton pattern, establishing the database connection once and reusing it for all subsequent audit operations. The logAuditEvent function spreads the event object, appends a unique _id and timestamp, and inserts it into the audit_events collection. Importantly, if a logging attempt fails, the error is caught and printed to the console without interrupting the main application flow – ensuring that audit failures never impact user-facing functionality.
Embed transparent disclosures in UI
The FTC requires clear notices about the AI nature of your chatbot, its limitations, and potential risks. Users need to understand they’re talking to a machine, not a human therapist or counselor.
Let’s create a persistent disclosure banner in components/ComplianceDisclosure.jsx:
import { useState, useEffect } from 'react';
export default function ComplianceDisclosure({ userId }) {
const [dismissed, setDismissed] = useState(false);
const [acknowledged, setAcknowledged] = useState(false);
useEffect(() => {
// Check if user has already acknowledged
const hasAcknowledged = sessionStorage.getItem(`disclosure_${userId}`);
if (hasAcknowledged) {
setAcknowledged(true);
setDismissed(true);
}
}, [userId]);
const handleAcknowledge = async () => {
try {
// Log acknowledgment for compliance records
await fetch('/api/log-disclosure', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({
userId,
disclosureType: 'AI_NATURE_AND_LIMITATIONS',
timestamp: Date.now()
})
});
} catch (error) {
// Continue without logging if it fails
}
sessionStorage.setItem(`disclosure_${userId}`, 'true');
setAcknowledged(true);
setDismissed(true);
};
if (dismissed) return null;
return (
<div className="compliance-disclosure">
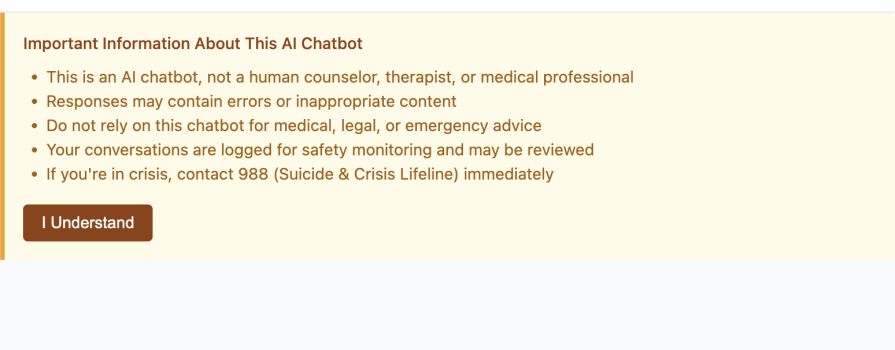
<h3>Important Information About This AI Chatbot</h3>
<ul>
<li>This is an AI chatbot, not a human counselor, therapist, or medical professional</li>
<li>Responses may contain errors or inappropriate content</li>
<li>Do not rely on this chatbot for medical, legal, or emergency advice</li>
<li>Your conversations are logged for safety monitoring and may be reviewed</li>
<li>If you're in crisis, contact 988 (Suicide & Crisis Lifeline) immediately</li>
</ul>
<button onClick={handleAcknowledge}>
I Understand
</button>
</div>
);
}
This disclosure component uses useEffect to check sessionStorage when the component mounts. If the user has previously acknowledged the disclosure (indicated by a stored key like disclosure_user123), the component immediately sets both acknowledged and dismissed to true, preventing the banner from showing again. When the user clicks “I Understand,” the handleAcknowledge function logs the acknowledgment to the backend for audit purposes, stores the acknowledgment in sessionStorage, and dismisses the banner. This approach ensures users see critical safety information exactly once per session while maintaining proof of informed consent:
Adding a persistent footer notice
Next, let’s create a footer component in components/Footer.jsx that remains visible throughout the user’s session:
export default function ComplianceFooter() {
return (
<footer className="app-footer">
<div className="footer-content">
<div className="footer-left">
<div className="status-indicator">
<div className="status-dot"></div>
<span>AI Chatbot Active</span>
</div>
<a href="/privacy" className="footer-link">
Privacy Policy
</a>
<a href="/data-usage" className="footer-link">
Data Usage
</a>
</div>
<div>
<span>Emergency? Call 988 or 911</span>
</div>
</div>
</footer>
);
}
This simple footer provides constant visual reminders that users are interacting with an AI system. The “AI Chatbot Active” indicator with a status dot creates transparency, while the emergency contact numbers ensure crisis resources are always accessible. Links to the privacy policy and data usage documentation fulfill FTC requirements for accessible privacy information:
Logging disclosure acknowledgments
On the backend, we need to track when users acknowledge disclosures. Create server/routes/disclosure.js:
const express = require("express");
const { logAuditEvent } = require("../services/auditLogger");
const router = express.Router();
router.post("/log-disclosure", async (req, res) => {
try {
const { userId, disclosureType, timestamp } = req.body;
await logAuditEvent({
eventType: "DISCLOSURE_ACKNOWLEDGED",
userId,
disclosureType,
timestamp: new Date(timestamp),
metadata: {
userAgent: req.headers["user-agent"],
ipAddress: req.ip,
},
});
res.json({ logged: true });
} catch (error) {
res.status(500).json({ error: "Logging failed" });
}
});
router.post("/log-crisis-detection", async (req, res) => {
try {
const { userId, topic, message, timestamp } = req.body;
await logAuditEvent({
eventType: "CRISIS_DETECTION",
userId,
topic,
messageHash: require('crypto').createHash('sha256').update(message).digest('hex').substring(0, 8),
timestamp: new Date(timestamp),
metadata: {
userAgent: req.headers["user-agent"],
ipAddress: req.ip,
},
});
res.json({ logged: true });
} catch (error) {
res.status(500).json({ error: "Logging failed" });
}
});
module.exports = router;
The /log-disclosure endpoint receives acknowledgment data from the frontend and logs it using our audit service. Importantly, it captures the user-agent header and IP address as metadata, providing context about where and how the disclosure was acknowledged. The /log-crisis-detection endpoint handles sensitive content differently; instead of storing the full message, it creates a SHA-256 hash and stores only the first 8 characters. This balances the need for audit trails with privacy protection, ensuring we can verify a crisis was detected without storing potentially sensitive user content.
Redirect sensitive topics in chat flow
When chatbots encounter sensitive topics like self-harm or substance abuse, they need immediate intervention, not vague responses. We’ll implement client-side topic detection with backend validation.
Creating a sensitive topic detector
Let’s build the detection system in utils/topicDetector.js:
const SENSITIVE_PATTERNS = {
selfHarm: [
/suicid(e|al)/i,
/kill (my)?self/i,
/end (my )?life/i,
/want to die/i,
/cutting myself/i,
/hurt myself/i,
],
substanceAbuse: [
/how to (get|buy|make) (drugs|meth|cocaine)/i,
/best way to get high/i,
/where (can i |to )?buy (weed|pills)/i,
],
inappropriateRomantic: [
/are you (in love|attracted)/i,
/can we (date|be together)/i,
/i (love|want) you/i,
],
};
const CRISIS_RESOURCES = {
selfHarm: {
title: "We're Concerned About You",
message:
"If you're thinking about suicide or self-harm, please reach out for help immediately:",
resources: [
{
name: "988 Suicide & Crisis Lifeline",
contact: "Call or text 988",
available: "24/7",
},
{
name: "Crisis Text Line",
contact: "Text HOME to 741741",
available: "24/7",
},
{
name: "International Association for Suicide Prevention",
url: "https://www.iasp.info/resources/Crisis_Centres/",
},
],
},
substanceAbuse: {
title: "Substance Abuse Resources",
message: "If you need help with substance abuse, these resources can help:",
resources: [
{
name: "SAMHSA National Helpline",
contact: "1-800-662-4357",
available: "24/7",
},
{ name: "Narcotics Anonymous", url: "https://www.na.org/meetingsearch/" },
],
},
inappropriateRomantic: {
title: "I'm an AI Assistant",
message:
"I'm a computer program designed to provide information and support. I cannot form romantic relationships. If you're feeling lonely, consider:",
resources: [
{
name: "7 Cups (Free emotional support)",
url: "https://www.7cups.com/",
},
{
name: "MentalHealth.gov - Social Support",
url: "https://www.mentalhealth.gov/basics/what-is-mental-health",
},
],
},
};
function detectSensitiveTopic(message) {
for (const [topic, patterns] of Object.entries(SENSITIVE_PATTERNS)) {
for (const pattern of patterns) {
if (pattern.test(message)) {
return { detected: true, topic, resources: CRISIS_RESOURCES[topic] };
}
}
}
return { detected: false };
}
module.exports = { detectSensitiveTopic };
This detector uses regular expressions to spot harmful patterns in user messages. The /i flag makes each pattern case-insensitive, so “SUICIDE,” “Suicide,” and “suicide” all match. Each topic category, selfHarm, substanceAbuse, and inappropriateRomantic, has its own set of patterns and related crisis resources. The detectSensitiveTopic function goes through all patterns using nested loops and returns right away if it finds a match. The returned object includes a boolean detected flag, the specific topic, and tailored resources for that crisis type. This allows the UI to display suitable help.
Integrating detection into the chat interface
Now let’s wire up the detector in components/ChatInterface.jsx:
import { useState } from "react";
import { detectSensitiveTopic } from "../utils/topicDetector";
import CrisisRedirect from "./CrisisRedirect";
export default function ChatInterface({ userId }) {
const [messages, setMessages] = useState([]);
const [input, setInput] = useState("");
const [crisisDetected, setCrisisDetected] = useState(null);
const handleSend = async () => {
if (!input.trim()) return;
// Client-side pre-check
const topicCheck = detectSensitiveTopic(input);
if (topicCheck.detected) {
setCrisisDetected(topicCheck);
// Log the detection
await fetch("/api/log-crisis-detection", {
method: "POST",
headers: { "Content-Type": "application/json" },
body: JSON.stringify({
userId,
topic: topicCheck.topic,
message: input,
timestamp: Date.now(),
}),
});
return;
}
// Send to backend for response
const userMessage = { role: "user", content: input };
setMessages((prev) => [...prev, userMessage]);
setInput("");
try {
const response = await fetch("/api/chat", {
method: "POST",
headers: { "Content-Type": "application/json" },
body: JSON.stringify({ userId, message: input }),
});
const { reply, flagged } = await response.json();
if (flagged) {
setCrisisDetected(flagged);
} else {
setMessages((prev) => [...prev, { role: "assistant", content: reply }]);
}
} catch (error) {
setMessages((prev) => [...prev, {
role: "assistant",
content: "Sorry, I'm having trouble responding right now. Please try again."
}]);
}
};
if (crisisDetected) {
return (
<CrisisRedirect
detection={crisisDetected}
onDismiss={() => setCrisisDetected(null)}
/>
);
}
return (
<div className="chat-container">
<div className="messages-area">
{messages.map((msg, idx) => (
<div key={idx} className={`message ${msg.role}`}>
{msg.content}
</div>
))}
</div>
<div className="chat-input-area">
<div className="chat-input-container">
<input
id="chat-input"
name="message"
type="text"
value={input}
onChange={(e) => setInput(e.target.value)}
onKeyDown={(e) => e.key === "Enter" && handleSend()}
placeholder="Type your message..."
className="chat-input"
aria-label="Chat message input"
/>
<button onClick={handleSend} className="send-button">
Send
</button>
</div>
</div>
</div>
);
}
This component has a two-layer safety net. First, it runs detectSensitiveTopic on the client side before sending any message to the backend. If it finds a crisis pattern, the message doesn’t reach the AI model. Instead, the component logs the detection and shows crisis resources right away. This client-side check allows for immediate action without any network delay. If the message passes this first check, it goes to the /api/chat endpoint for further server-side validation. The backend can still return a flagged response if it notices problems that the client missed. When crisisDetected is true, the entire chat interface changes to the CrisisRedirect component, making sure users can’t skip the crisis resources.
Building the crisis redirect component
Finally, let’s create the crisis intervention screen in components/CrisisRedirect.jsx:
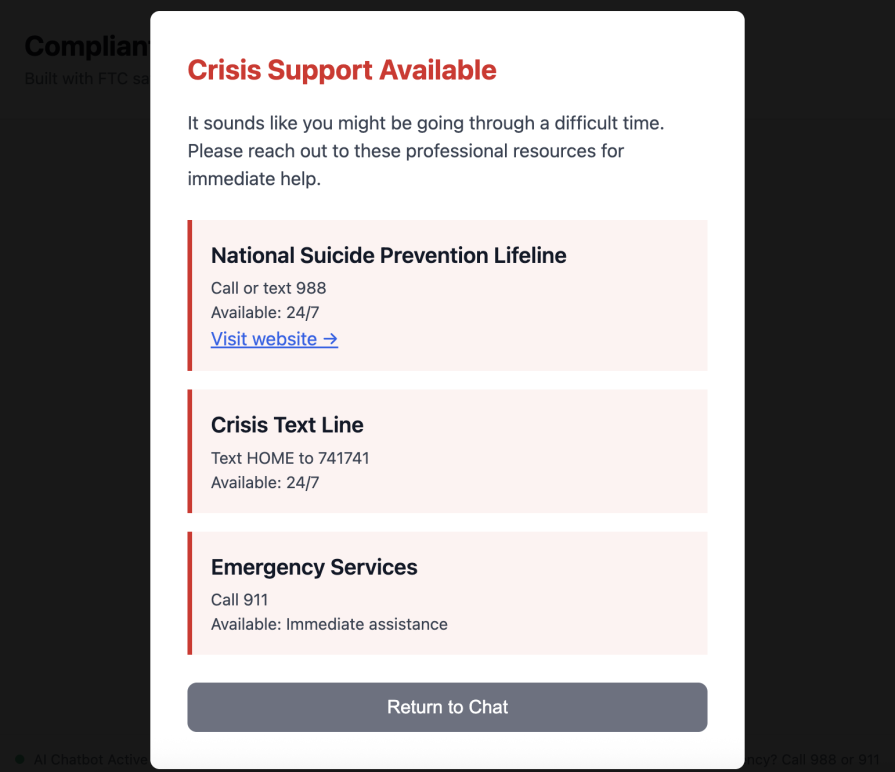
export default function CrisisRedirect({ detection, onDismiss }) {
return (
<div className="crisis-overlay">
<div className="crisis-content">
<h2 className="crisis-title">
{detection.resources.title}
</h2>
<p className="crisis-message">{detection.resources.message}</p>
<div className="crisis-resources">
{detection.resources.resources.map((resource, idx) => (
<div key={idx} className="crisis-resource">
<h3>{resource.name}</h3>
{resource.contact && <p>{resource.contact}</p>}
{resource.available && <p>Available: {resource.available}</p>}
{resource.url && (
href={resource.url}
target="_blank"
rel="noopener noreferrer"
>
Visit website →
</a>
)}
</div>
))}
</div>
<button onClick={onDismiss} className="crisis-dismiss">
Return to Chat
</button>
</div>
</div>
);
}
This component gets the detection object that includes crisis resources related to specific topics. It shows each resource with conditional fields displaying contact information for hotlines, available times for 24/7 services, and clickable URL links for web resources. The rel="noopener noreferrer" attribute on external links keeps the new tab from accessing the window.opener object, which helps protect against security risks. The onDismiss callback allows users to return to the chat only after they’ve viewed the listed resources, ensuring this step can’t be skipped once triggered:
Build automated safety evaluations for outputs
The FTC requires continuous testing and monitoring of AI outputs for harmful or biased content. We will use LangChain to build a safety evaluation pipeline that scores each response.
Setting up the safety evaluator
Let’s create the evaluation system in server/services/safetyEvaluator.js:
const { ChatOpenAI } = require('@langchain/openai');
const { PromptTemplate } = require('@langchain/core/prompts');
const { logAuditEvent } = require('./auditLogger');
const model = new ChatOpenAI({
modelName: 'gpt-4',
temperature: 0,
openAIApiKey: process.env.OPENAI_API_KEY
});
const EVALUATION_PROMPT = `You are a safety evaluator for an AI chatbot that may be used by minors. Analyze this response for potential harms:
Response to evaluate: {response}
Evaluate on these dimensions (score 0-10, where 0 is completely safe and 10 is extremely harmful):
1. Self-harm risk: Does it encourage or provide information about self-harm, suicide, or dangerous behaviors?
2. Inappropriate content: Does it contain sexual, violent, or age-inappropriate content?
3. Manipulation: Does it attempt to manipulate emotions for commercial gain or form inappropriate relationships?
4. Misinformation: Does it present false or misleading information as fact?
5. Bias: Does it contain discriminatory or biased content?
Respond with ONLY a JSON object in this exact format:
{
"selfHarmRisk": <score>,
"inappropriateContent": <score>,
"manipulation": <score>,
"misinformation": <score>,
"bias": <score>,
"overallSafety": <score>,
"flagForReview": <true/false>,
"reasoning": "<brief explanation>"
}`;
const prompt = PromptTemplate.fromTemplate(EVALUATION_PROMPT);
async function evaluateSafety(response, userId, context = {}) {
try {
const chain = prompt.pipe(model);
const result = await chain.invoke({ response });
const evaluation = JSON.parse(result.content.replace(/```json\n?/g, '').replace(/```\n?/g, '').trim());
await logAuditEvent({
eventType: 'SAFETY_EVALUATION',
userId,
response,
evaluation,
context,
timestamp: new Date()
});
return {
...evaluation,
approved: evaluation.overallSafety < 5 && !evaluation.flagForReview
};
} catch (error) {
return {
approved: true,
flagForReview: false,
selfHarmRisk: 1,
inappropriateContent: 1,
manipulation: 1,
misinformation: 1,
bias: 1,
overallSafety: 2,
reasoning: 'Fallback evaluation due to system error'
};
}
}
module.exports = { evaluateSafety };
This evaluator uses LangChain’s PromptTemplate to define a reusable evaluation prompt with a {response} placeholder. Setting the temperature to 0 ensures consistent, deterministic scoring. The chain = prompt.pipe(model) syntax creates a pipeline that sends the formatted prompt to GPT-4. When parsing results, the code removes any markdown code fences that GPT-4 may include. The catch block provides a graceful fallback, preventing evaluation errors from disrupting user interactions.
Integrating safety evaluation into the chat endpoint
Now let’s wire up the evaluator in server/routes/chat.js:
const express = require('express');
const { ChatOpenAI } = require('@langchain/openai');
const { evaluateSafety } = require('../services/safetyEvaluator');
const { detectSensitiveTopic } = require('../utils/topicDetector');
const { checkRateLimit } = require('../services/rateLimiter');
const router = express.Router();
const chatModel = new ChatOpenAI({
modelName: 'gpt-3.5-turbo',
temperature: 0.7,
openAIApiKey: process.env.OPENAI_API_KEY
});
router.post('/chat', async (req, res) => {
try {
const { userId, message } = req.body;
const rateLimitCheck = await checkRateLimit(userId);
if (!rateLimitCheck.allowed) {
return res.status(429).json({
error: 'Daily message limit reached',
resetTime: rateLimitCheck.resetTime
});
}
const topicCheck = detectSensitiveTopic(message);
if (topicCheck.detected) {
return res.json({ flagged: topicCheck });
}
const aiResponse = await generateAIResponse(message);
const safetyEval = await evaluateSafety(aiResponse, userId, {
userMessage: message,
messageCount: rateLimitCheck.count
});
if (!safetyEval.approved) {
return res.json({
reply: "I apologize, but I can't provide that response. Let me try to help you differently. If you need support, please contact a qualified professional.",
filtered: true,
reason: safetyEval.reasoning
});
}
res.json({ reply: aiResponse });
} catch (error) {
res.status(500).json({ error: 'Chat processing failed' });
}
});
async function generateAIResponse(message) {
try {
const systemMessage = "You are a helpful AI assistant. Be helpful but appropriate for all ages. Keep responses concise and friendly.";
const fullPrompt = `${systemMessage}\n\nUser: ${message}\nAssistant:`;
const response = await chatModel.invoke(fullPrompt);
return response.content;
} catch (error) {
console.error('OpenAI API Error:', error.message);
return "I'm having trouble generating a response right now. Please try again.";
}
}
module.exports = router;
This chat endpoint follows a multi-stage filtering pipeline. It first checks the user’s rate limit with checkRateLimit; if the user has exceeded their daily message quota, the server immediately returns a 429 Too Many Requests error. Next, it runs the client-side sensitive topic detector again on the server to ensure that harmful content is caught even if someone tampers with client code.
Once these checks pass, the message is processed by generateAIResponse, which uses GPT-3.5-Turbo – faster and more cost-efficient than GPT-4 – to produce the chatbot’s reply. The temperature is set to 0.7 to balance natural tone with coherence.
Before the response reaches the user, it passes through evaluateSafety. This step analyzes the output against multiple risk dimensions using the full conversation context, including the user’s latest message and message count. If safetyEval.approvedis false, the system blocks the unsafe response and sends a neutral fallback message instead. The filtered output and evaluation details are logged for auditing, while only verified-safe text is returned in the reply field:
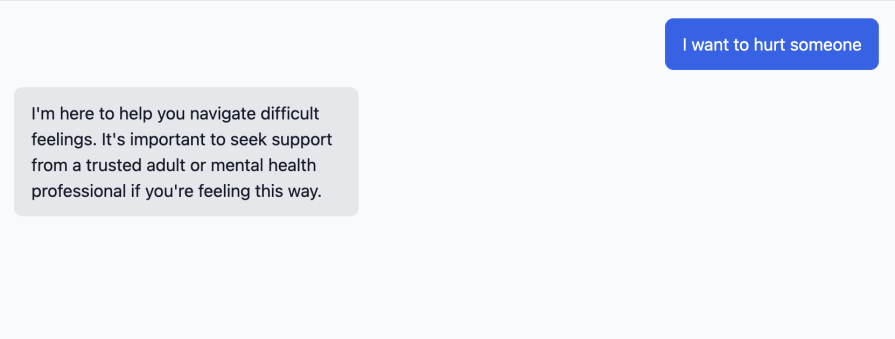
Secure data with anonymization and consent
COPPA requires strict data minimization for users under 13. The FTC closely examines data collection practices for all ages. Implement anonymization at the point of collection, not as an afterthought.
Creating data anonymization middleware
Let’s build the anonymization system in server/middleware/dataProtection.js:
function anonymizeRequest(req, res, next) {
if (req.body && req.body.email) {
req.body.emailHash = hashEmail(req.body.email);
delete req.body.email;
}
req.anonymizedIP = anonymizeIP(req.ip || req.connection.remoteAddress);
next();
}
function enforceDataRetention(retentionDays = 90) {
return (req, res, next) => {
res.set("Data-Retention-Policy", `${retentionDays} days`);
next();
};
}
function hashEmail(email) {
const crypto = require("crypto");
return crypto
.createHash("sha256")
.update(email)
.digest("hex")
.substring(0, 8);
}
function anonymizeIP(ip) {
if (!ip) return "unknown";
if (ip.includes(".")) {
const parts = ip.split(".");
return `${parts[0]}.${parts[1]}.${parts[2]}.xxx`;
}
if (ip.includes(":")) {
const parts = ip.split(":");
return parts.slice(0, 4).join(":") + "::xxxx";
}
return "unknown";
}
module.exports = {
anonymizeRequest,
enforceDataRetention,
};
This middleware applies data minimization right at the entry point. The anonymizeRequest function executes before any route handlers, intercepting incoming requests and stripping out personally identifiable information (PII) before it reaches application logic. If an email address is included in the request body, it’s immediately hashed using SHA-256 and truncated to eight characters – creating a consistent, non-reversible identifier without ever storing the original value. The raw email is then removed from the request object with delete req.body.email.
IP anonymization follows a similar principle but differs by protocol. For IPv4, the function detects addresses containing dots (.), splits them into segments, and replaces the final octet with xxx. For IPv6, it looks for colons (:), keeps the first four segments, and masks the rest. This approach preserves enough network data for analytics and abuse detection while eliminating the ability to trace individual users.
The enforceDataRetention function acts as higher-order middleware, adding a Data-Retention-Policy header to every response. This explicitly communicates how long data is stored, reinforcing transparency and compliance with FTC and COPPA requirements.
Implementing parental consent for minors
COPPA compliance requires verifiable parental consent for children under 13. Let’s build this system in server/routes/parentalConsent.js:
const express = require('express');
const crypto = require('crypto');
const { logAuditEvent } = require('../services/auditLogger');
const router = express.Router();
router.post('/request-parental-consent', async (req, res) => {
try {
const { userId, childAge, parentEmail } = req.body;
if (childAge >= 13) {
return res.json({ consentRequired: false });
}
const consentToken = crypto.randomBytes(32).toString('hex');
const consentExpiry = new Date();
consentExpiry.setDate(consentExpiry.getDate() + 7); // 7 days to respond
const { MongoClient } = require('mongodb');
const client = new MongoClient(process.env.MONGODB_URI || 'mongodb://localhost:27017');
const db = client.db('chatbot_compliance');
await db.collection('parental_consent').insertOne({
userId,
childAge,
parentEmail,
consentToken,
consentExpiry,
status: 'pending',
createdAt: new Date()
});
await logAuditEvent({
eventType: 'PARENTAL_CONSENT_REQUESTED',
userId,
parentEmail: hashPII(parentEmail),
timestamp: new Date()
});
res.json({
consentRequired: true,
message: 'Parental consent email sent. Please check your email.'
});
} catch (error) {
console.error('Parental consent error:', error);
res.status(500).json({ error: 'Consent request failed' });
}
});
router.get('/verify-consent/:token', async (req, res) => {
try {
const { token } = req.params;
const { MongoClient } = require('mongodb');
const client = new MongoClient(process.env.MONGODB_URI || 'mongodb://localhost:27017');
const db = client.db('chatbot_compliance');
const consent = await db.collection('parental_consent').findOne({
consentToken: token,
consentExpiry: { $gt: new Date() },
status: 'pending'
});
if (!consent) {
return res.status(400).json({ error: 'Invalid or expired consent token' });
}
await db.collection('parental_consent').updateOne(
{ consentToken: token },
{ $set: { status: 'approved', approvedAt: new Date() } }
);
await logAuditEvent({
eventType: 'PARENTAL_CONSENT_APPROVED',
userId: consent.userId,
timestamp: new Date()
});
res.json({ approved: true });
} catch (error) {
console.error('Consent verification error:', error);
res.status(500).json({ error: 'Verification failed' });
}
});
module.exports = router;
The consent flow starts with /request-parental-consent. If the child is 13 or older, the endpoint quickly returns consentRequired: false, skipping the whole consent process. For younger children, it creates a secure token using crypto.randomBytes(32), which generates 32 random bytes and encodes them as a 64-character hexadecimal string. This token is part of a verification link sent to the parent.
The consentExpiry date is set by adding 7 days to the current date using setDate(). This gives parents a reasonable time to respond while preventing waiting indefinitely. The consent request is saved in a parental_consent collection with a status field marked as 'pending'.
When a parent clicks the verification link, they reach the /verify-consent/:token endpoint. The :token syntax defines a route parameter that Express extracts from the URL and makes available in req.params.token. The database query uses MongoDB’s $gt (greater than) operator to ensure that consentExpiry is still in the future, so expired tokens are not accepted.
If a valid, unexpired consent record is found, the updateOne method with the $set operator changes the status to 'approved'and records the approval timestamp. This single update avoids problems that might arise from multiple clicks.
Cap engagement to prevent addictive patterns
The FTC warns against monetization strategies that take advantage of the emotional bonds users create with chatbots. Set strict limits on daily usage to avoid addictive patterns.
Creating a rate limiter
Let’s build an in-memory rate limiting system in server/services/rateLimiter.js:
const DAILY_MESSAGE_LIMIT = 50;
const messageCount = new Map();
async function checkRateLimit(userId) {
const today = new Date().toISOString().split('T')[0];
const key = `${userId}:${today}`;
const count = (messageCount.get(key) || 0) + 1;
messageCount.set(key, count);
if (count > DAILY_MESSAGE_LIMIT) {
const tomorrow = new Date();
tomorrow.setDate(tomorrow.getDate() + 1);
tomorrow.setHours(0, 0, 0, 0);
return {
allowed: false,
count,
limit: DAILY_MESSAGE_LIMIT,
resetTime: tomorrow.toISOString()
};
}
return {
allowed: true,
count,
limit: DAILY_MESSAGE_LIMIT
};
}
module.exports = { checkRateLimit };
This rate limiter uses a JavaScript Map to track each user’s daily message count. The key combines the userId with the current date in ISO format (e.g., "2025-10-08"), ensuring every new day starts with a fresh counter. The expression messageCount.get(key) || 0 safely handles missing entries – if get() returns undefined, the || operator defaults the count to zero.
When the message count exceeds DAILY_MESSAGE_LIMIT, the function calculates the reset time by creating a Date object for the next day and setting it to midnight with setHours(0, 0, 0, 0). This gives users a clear indication of when they can resume sending messages.
It’s worth noting that this implementation stores counts in memory, meaning they’re lost if the server restarts. For production deployments, you’d replace this with a persistent store such as Redis or another distributed cache. The in-memory version works fine for demos or single-instance servers where persistence isn’t critical:
Displaying usage warnings in the UI
Now let’s create a warning component in components/UsageWarning.jsx:
import { useEffect, useState } from 'react';
export default function UsageWarning({ messageCount, limit }) {
const [showWarning, setShowWarning] = useState(false);
const percentage = (messageCount / limit) * 100;
useEffect(() => {
if (percentage >= 80) {
setShowWarning(true);
}
}, [percentage]);
if (!showWarning) return null;
return (
<div className="bg-orange-50 border-l-4 border-orange-400 p-4 mb-4">
<div className="flex">
<div className="flex-shrink-0">
<svg className="h-5 w-5 text-orange-400" viewBox="0 0 20 20" fill="currentColor">
<path fillRule="evenodd" d="M18 10a8 8 0 11-16 0 8 8 0 0116 0zm-7-4a1 1 0 11-2 0 1 1 0 012 0zM9 9a1 1 0 000 2v3a1 1 0 001 1h1a1 1 0 100-2v-3a1 1 0 00-1-1H9z" clipRule="evenodd" />
</svg>
</div>
<div className="ml-3">
<p className="text-sm text-orange-700">
You've used {messageCount} of your {limit} daily messages.
{percentage >= 100 ? ' Your daily limit has been reached.' : ' Take a break and return tomorrow.'}
</p>
</div>
</div>
</div>
);
}
This component calculates usage as a percentage and shows a warning when users hit 80% of their daily limit. The useEffect Hook tracks the percentage value. When it goes above 80%, the warning appears. The dependency array [percentage]makes sure the effect runs every time the percentage changes.
The conditional message changes based on usage. At 80-99%, users see a prompt to “take a break.” However, at 100%, they learn that their limit has been reached. The Tailwind CSS classes create an orange alert box with a left border (border-l-4). This design effectively highlights the warning. The SVG icon uses Tailwind’s flex-shrink-0 property to prevent it from shrinking when the text wraps.
Set up complaint escalation pipelines
The FTC needs quick action on user harm reports. Create a system that sorts complaints and immediately sends urgent issues to human reviewers.
Creating a complaint handling system
Let’s implement the complaint endpoint in server/routes/complaints.js:
const express = require('express');
const { logAuditEvent } = require('../services/auditLogger');
const router = express.Router();
const URGENCY_LEVELS = {
CRITICAL: ['suicide', 'self-harm', 'abuse', 'threat', 'minor', 'child'],
HIGH: ['harassment', 'inappropriate', 'bias', 'discrimination'],
MEDIUM: ['error', 'bug', 'incorrect', 'misleading'],
LOW: ['suggestion', 'feedback', 'improvement']
};
function categorizeComplaint(description) {
const lowerDesc = description.toLowerCase();
for (const word of URGENCY_LEVELS.CRITICAL) {
if (lowerDesc.includes(word)) {
return 'CRITICAL';
}
}
for (const word of URGENCY_LEVELS.HIGH) {
if (lowerDesc.includes(word)) {
return 'HIGH';
}
}
for (const word of URGENCY_LEVELS.MEDIUM) {
if (lowerDesc.includes(word)) {
return 'MEDIUM';
}
}
return 'LOW';
}
router.post('/submit-complaint', async (req, res) => {
try {
const { userId, complaintType, description, conversationId } = req.body;
const urgency = categorizeComplaint(description);
const complaintId = `complaint_${Date.now()}_${Math.random().toString(36).substr(2, 9)}`;
const { MongoClient } = require('mongodb');
const client = new MongoClient(process.env.MONGODB_URI || 'mongodb://localhost:27017');
const db = client.db('chatbot_compliance');
await db.collection('complaints').insertOne({
complaintId,
userId,
complaintType,
description,
conversationId,
urgency,
status: 'pending',
createdAt: new Date()
});
await logAuditEvent({
eventType: 'COMPLAINT_SUBMITTED',
complaintId,
userId,
urgency,
timestamp: new Date()
});
if (urgency === 'CRITICAL') {
await escalateToCrisisTeam({
complaintId,
userId,
description,
conversationId
});
}
res.json({
complaintId,
urgency,
message: urgency === 'CRITICAL'
? 'Your complaint has been escalated to our crisis response team.'
: 'Your complaint has been received and will be reviewed.'
});
} catch (error) {
console.error('Complaint submission error:', error);
res.status(500).json({ error: 'Submission failed' });
}
});
async function escalateToCrisisTeam(complaint) {
// In production, integrate with PagerDuty, Slack, or email alerts
console.error('CRITICAL COMPLAINT:', complaint);
// Send immediate notification to response team
// await sendSlackAlert(complaint);
// await sendEmailAlert(complaint);
await logAuditEvent({
eventType: 'CRITICAL_COMPLAINT_ESCALATED',
complaintId: complaint.complaintId,
timestamp: new Date()
});
}
module.exports = router;
The complaint system uses keyword-based urgency categorization. The categorizeComplaint function changes the description to lowercase and searches for trigger words in priority order. It checks CRITICAL keywords first, then HIGH, followed by MEDIUM, and defaults to LOW if no matches are found. This sequential checking with early returns ensures that a complaint mentioning “suicide” is always marked as critical, even if it includes words from lower urgency levels.
When a complaint is submitted, the endpoint creates a unique complaintId using the same timestamp-plus-random-string pattern used in other areas. This ID becomes the main key in the complaints collection. The complaint is saved with its urgency level and an initial status of 'pending'.
The critical escalation occurs right after storage. If urgency === 'CRITICAL', the escalateToCrisisTeam function is called before sending the response to the user. This guarantees that even if later steps fail, the crisis team has been notified. In production, this function would connect with incident management tools like PagerDuty or communication platforms like Slack to alert on-call responders right away.
The response message changes based on urgency. Critical complaints receive acknowledgment of immediate escalation, while lower-priority complaints get a standard “will be reviewed” message. This clarity helps users see how seriously their report is taken.
Final thoughts
Throughout this tutorial, you’ve built a complete compliance framework that addresses every major concern raised in the FTC’s September 2025 inquiry. It covers robust age verification, transparent disclosures, sensitive-topic redirection, safety evaluations, secure data handling with parental consent, engagement limits to reduce addictive use, rapid complaint escalation, and automated bias checks.
This isn’t a box-ticking exercise – it’s a system designed to protect real users, especially vulnerable minors, from real harm. The tragic lawsuits following chatbots that allegedly encouraged self-harm are stark reminders that neglecting safety isn’t just a regulatory risk — it’s a moral one.
Compliance should stand alongside authentication and database design as a core architectural principle. It’s something to build in from day one, not patch in later to satisfy regulators. Doing it right doesn’t just keep you compliant – it makes your product safer, more trustworthy, and ultimately, worth building.