Risky Bulletin Newsletter
October 22, 2025
Written by

Catalin Cimpanu
News Editor
** * This newsletter is brought to you by * ** Dropzone ** * . You can subscribe to an audio version of this newsletter as a podcast by searching for “Risky Business” in your podcatcher or subscribing via * ** this RSS feed ** * . * **
Security researchers have spotted a second self-propagating worm that hit the DevOps space within the span of a month. The new threat is named GlassWorm and primarily targets the VS Code extensions space.
It is the second such threat after the [Shai-Hulud worm ](https://unit42.paloaltonetworks.com/npm-supply-c…
Risky Bulletin Newsletter
October 22, 2025
Written by

Catalin Cimpanu
News Editor
** * This newsletter is brought to you by * ** Dropzone ** * . You can subscribe to an audio version of this newsletter as a podcast by searching for “Risky Business” in your podcatcher or subscribing via * ** this RSS feed ** * . * **
Security researchers have spotted a second self-propagating worm that hit the DevOps space within the span of a month. The new threat is named GlassWorm and primarily targets the VS Code extensions space.
It is the second such threat after the Shai-Hulud worm that hit the npm JavaScript package repo in mid-September.
GlassWorm was spotted by Koi Security . It was first seen on the unofficial OpenVSX marketplace for VS Code extensions, but later spread to the official Microsoft VS Code store as well.
At the time of writing, the worm has spread and infected 15 extensions on OpenVSX and one on the official store. See this live infection status page .
The worm works by infecting a developer’s computer when they install one of the infected extensions. Its main purpose is cryptocurrency theft, which it does by searching for 49 cryptocurrency browser extensions and then emptying their funds.
After that, the malware installs a SOCKS proxy server on the developer’s system to turn their PC into a node in a proxy network, and also installs a hidden HNC server to grant attackers remote access at will sometime in the future.
Last, GlassWorm also searches and exfiltrates access credentials for GitHub accounts, Git repos, and npm and OpenVSX accounts. It uses these credentials to access the accounts and inject its code into a developer’s projects.
Right now, Koi Security has confirmed cases where GlassWorm has spread to other VS Code extensions, but don’t be surprised if it spreads to npm and other libraries in the coming days.
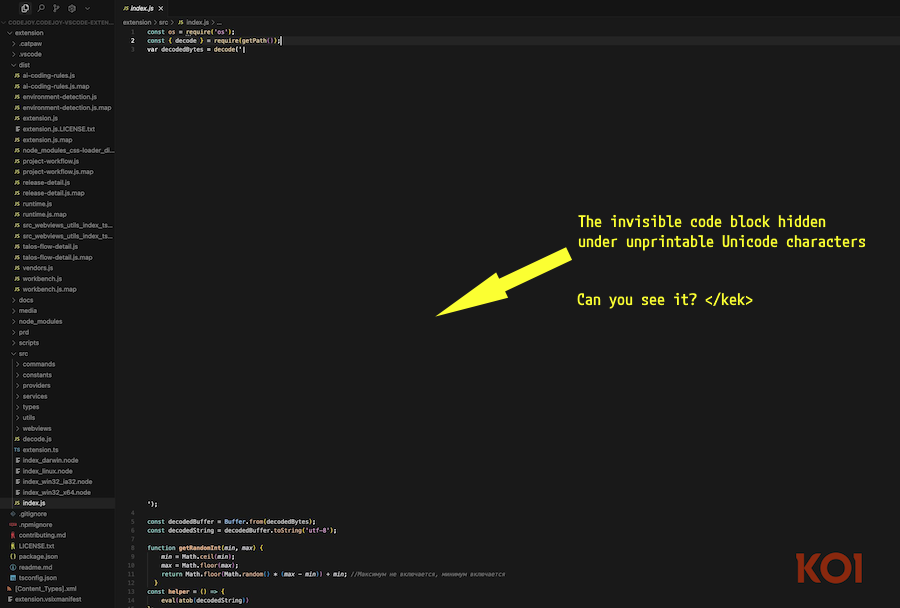
Koi researchers have described the malware as highly sophisticated because of its use of the blockchain for C&C communications, the use of Google Calendar as a secondary, backup C&C channel, and the use of unprintable Unicode characters to hide its malicious code from human reviewers.
GlassWorm is certainly something way more professional and more thought-through than most malware that has targeted npm and PyPI over the past two years.
It appears the Shai-Hulud incident might have encouraged other malware developers to play around with the concept of a fast-spreading capability, something that’s rarely seen in the wild these days outside the IoT DDoS botnet ecosystem.
Shai-Hulud and GlassWorm are ideal for quick hit-and-run wallet cash-outs, where persistence and intelligence gathering are not of importance, and only the volume of stolen assets matters at the end of the day.
** * Risky Business Podcasts * **
- The main ** Risky Business ** podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm! *
** Breaches, hacks, and security incidents **
** F5 breach began in 2023: ** The breach at American tech company F5 began in late 2023, far earlier than previously thought, according to a new Bloomberg report. The hackers breached the company after exploiting its own products. F5 staff allegedly failed to follow the cybersecurity guides it passed to customers. The breach was discovered in August this year. Days after the hack, the company announced the end-of-life of two of its BIG-IP products. [ * h/t Dr. David McBride * ]
** KT CEO to resign after major breach: ** The CEO of Korea Telecom (KT) will resign from his post after the company concludes an investigation into a recent security breach. Hackers stole almost $170,000 from customer accounts via the company’s micro-payments platform. The thefts have been traced to fake mobile towers installed across the country that harvested customer information. KT allegedly tried to hide the breach and is now facing a probe for obstructing a government investigation. [ * Additional coverage in the * Chosun Daily ]
** Handala leaks Israeli military data: ** The Handala hacking group has leaked the names and other personal details of 17 Israeli senior military scientists. The group claims the 17 have helped build Israel’s war machine. A week earlier, Handala also doxed 15 Israeli officials accused of war crimes. Previous reporting has linked the Handala group to Iran’s intelligence services. [ * Additional coverage in the * Tehran Times ]
** NSA leak: ** Hackers have leaked the alleged data of NSA and other US government officials. This includes employees from the US Air Force, Defense Intelligence Agency, the Federal Trade Commission, Federal Aviation Administration, Centers for Disease Control and Prevention, and the Bureau of Alcohol, Tobacco, Firearms, and Explosives. This is the same group that leaked ICE and DHS data over the weekend. [ * Additional coverage in * 404 Media ]
** Askul halts online orders after cyberattack: ** Japanese retailer Askul has halted online orders due to a cyberattack. Several smaller retailer chains that depend on Askul have also shut down online ordering systems, as well. The incident took place on Sunday and is a ransomware attack. [ * Additional coverage in the * Japan Times ]
** Dodo breach: ** Hackers have gained access to 1,600 email accounts of Dodo customers. The incident took place on Friday and led to at least 34 cases of SIM swapping attacks against 34 Dodo mobile accounts. The Australian internet service provider has shut down its email system to prevent further attacks. [ * Additional coverage in * iTnews ]
** Xubuntu website hacked: ** Hackers have breached the website for the Xubuntu distro to add a Windows-based crypto-clipper to its downloads section. Putting Windows malware in a Linux distro is peak stupidity. Talk about wasting your time! [ * Additional coverage in * OMG! Ubuntu * and * vx-underground ]
** Trenchant leak and spyware attack: ** A former developer for an American surveillance vendor was targeted with iOS spyware. Jay Gibson says he was notified by Apple of an attack with mercenary spyware after he left Trenchant. Gibson developed iOS exploits for the company. He told TechCrunch * * he was fired after being unfairly blamed for a leak of sensitive documents from the company’s Chrome exploit team.
** Typus Finance crypto-heist: ** Hackers have stolen $3.44 million worth of crypto-assets from DeFi platform Typus Finance. The hack took place last week, when hackers exploited a vulnerability to drain funds from one of its smart contracts. Typus says it filed a police report less than two hours after it was hacked.
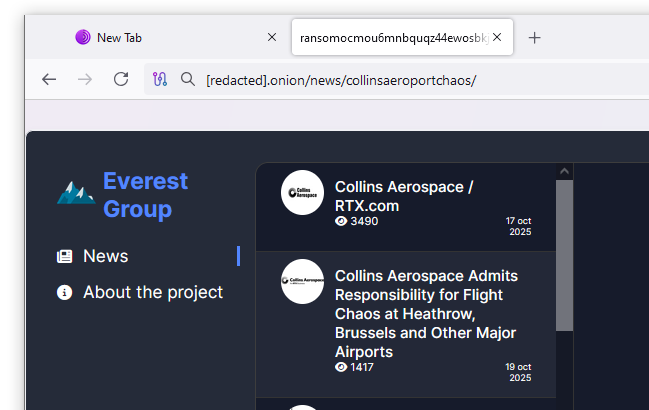
** Everest claims Collins incident: ** The Everest ransomware group has taken credit for the incident at Collins Aerospace that crippled airports all over Europe last month. The group claims it stole 50GB of files from the company. It plans to publish the files by Friday if Collins doesn’t pay a ransom. UK authorities arrested a man from West Sussex for his role in the ransomware attack. [ * h/t Nejoku23 * ]
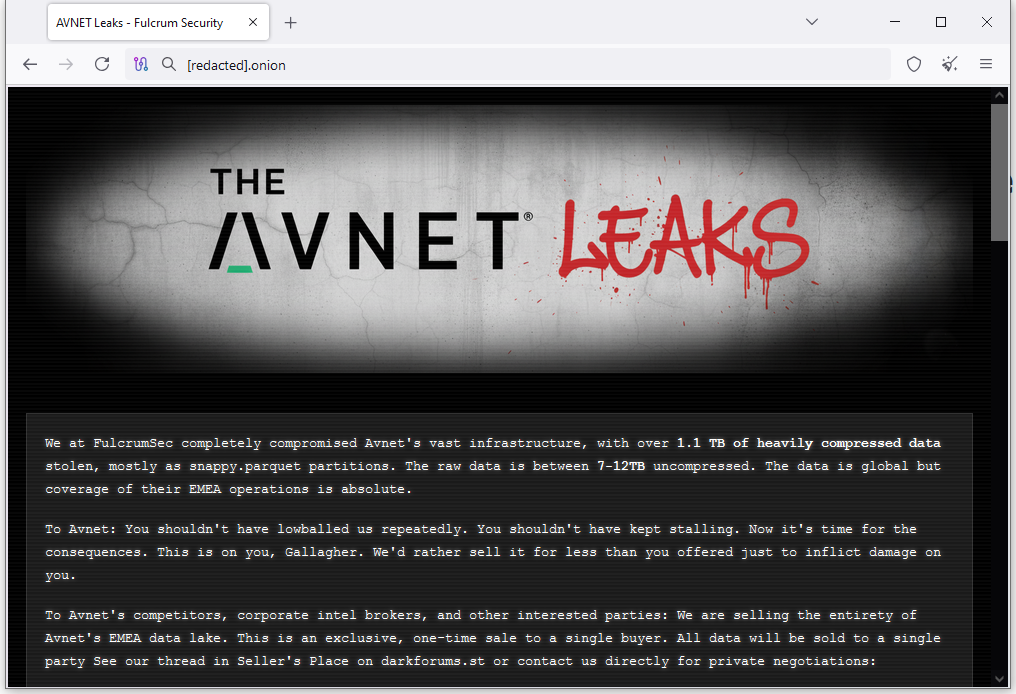
** Fulcrumsec claims Avnet hack: ** A new hacking group named Fulcrumsec claimed responsibility for hacking electronic components distributor Avnet. The group launched a dedicated website on the dark web, where it leaked some of the company’s data. The group leaked the data after Avnet allegedly stalled and lowballed their extortion attempts. Avnet confirmed the hack two weeks ago.
** General tech and privacy **
** FD-SOI: ** The French Alternative Energies and Atomic Energy Commission (CEA) and Soitec launched FD-SOI (Fully Depleted Silicon-on-Insulator) on Monday, a new technology to protect automotive microchips against fault injection attacks, such as voltage surges or laser pulses.
** No-IP blocked in Spain: ** Spanish internet service providers are blocking access to the No-IP dynamic DNS service with an HTTP error code 451. The error is usually shown when sites are taken down due to legal reasons. Spain is widely known for severe internet filtering to fight off piracy. [ * Additional coverage in * TorrentFreak ]
** ICE’s use of pen registers: ** Forbes’ Thomas Brewster looks at how ICE is using pen registers to get metadata from WhatsApp and track who a target is communicating with. In this particular case, ICE identified people conversing with a Guatemalan woman suspected of selling forged documents.
** Massive AWS outage: ** AWS had a massive outage that impacted its infamous US-EAST-1 Region, meaning a considerable chunk of the modern internet went down on Monday for hours. A whopping 140 AWS services had disruptions.

** OpenAI launches Atlas browser: ** AI company OpenAI has launched an AI-powered browser named ChatGPT Atlas . [ * Additional coverage in * The Verge ]
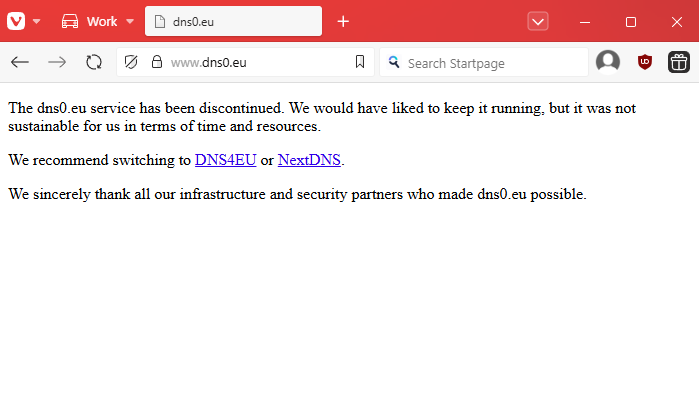
** DNS0 shuts down: ** Private DNS service DNS0.EU shut down last week, citing the unsustainable costs of running the service.
** Government, politics, and policy **
** Cloud SRM guide: ** Australia’s cybersecurity agency has shared a guide on properly setting up cloud services and what falls into the customer and cloud provider’s responsibilities.
** Italy probes intel chiefs on spying scandal: ** Italian investigators have questioned the heads of Italy’s two intelligence agencies (AISE, AISI) on the use of spyware against journalists, business people, and even priests. [ * Additional coverage in * Alanews ] [ * h/t Lorenzo Franceschi-Bicchierai * ]
** Another useless probe: ** US House Democrats are seeking answers from DHS Secretary Kristi Noem on the agency reassigning CISA cyber staff to immigration enforcement work, arguing that Noem violated the Antideficiency Act. As in similar past hearings, they’ll likely get mocked or ignored by an increasingly authoritarian Republican party. Sorry to burst your bubble, American readers! [ * Additional coverage in * NextGov ]
** FCC moves to ban HKT: ** The US Federal Communications Commission has started the process of banning HKT, a Hong Kong-based telco, from the US telecommunications network. The agency says HKT is an affiliate of China Unicom, a telco banned in previous years.
** Russia looking at age verification, too: ** The Russian government is exploring the idea of introducing age verification checks similar to the ones used in the West. Russian internet users may soon be required to show a passport, a driver’s license, or banking information to access certain websites. The age checks will be enforced on websites that show adult content, scenes of violence, contain profanity, propaganda, or antisocial behavior. The proposed age checks are part of a larger Russian government goal of allowing users on the internet in the next three years only after they’ve identified themselves. [ * Additional coverage in * RIA Novosti * and * Gazeta.ru ]
** The Netherlands stop sharing some intel with the US: ** For pretty f***ing obvious reasons, the two Dutch intelligence services, the AIVD and the MIVD, have stopped sharing some threat intelligence with their US counterparts. It’s unclear if this impacts collaboration on cybersecurity matters. [ * Additional coverage in * IntelNews ]
- In this ** Risky Business sponsor interview ** , Tom Uren talks to Edward Wu, CEO and founder of Dropzone AI, about a study that measured how AI practically helps SOC analysts triage real-world problems. Analysts were faster, more accurate, and got less tired with AI assistance. Edward thinks the technology won’t replace human analysts, but will speed their skill development. *
** Arrests, cybercrime, and threat intel **
** London SMS blaster sentenced: ** A 31-year-old man was sentenced to 24 weeks in prison for using an SMS blaster to spam London underground commuters. Kong Ji Chen was arrested in July by the British Transport Police after loitering for hours in metro stations without taking any trains. He was carrying an SMS blaster inside a large green suitcase. Chen initially claimed he was given the suitcase and didn’t know about the device, but eventually pleaded guilty.
** Belarus arrests cyber kingpin: ** Belarus authorities have arrested a 25-year-old for running a cybercrime service that traded and registered bank accounts. The service had more than 1,700 users who traveled and registered bank accounts in different geographical areas. Bank accounts were registered across several former Soviet states and used to launder stolen funds. Seventy of the main suspect’s accomplices were also detained. [ * Additional coverage in * DailyNews.by ]
** Massive WatchGuard Firebox exposure: ** According to the Shadowserver Foundation , more than 71,000 WatchGuard Firebox firewalls are exposed on the internet and vulnerable to a recently patched RCE vulnerability tracked as CVE-2025-9242 .
** Microsoft Copilot Studio abuse: ** DataDog researchers look at how threat actors are abusing the Microsoft Copilot Studio as a wrapper to disguise token thefts in phishing operations.
** Scattered LAPSUS$ Hunters update: ** PAN’s Unit42 covers some of the crazy talk on the Telegram channel of Scattered LAPSUS$ Hunters, the group that hacked Salesforce and is now leaking US government employee details. It’s a descent into madness over there.
** Monolock ransomware: ** Threat actors are selling a new ransomware strain named Monolock on underground hacking forums.
** Meta scam account takedowns: ** Meta’s security team has suspended more than eight million Facebook and Instagram accounts this year that were linked to online scams. The company linked the accounts to scam compounds in Myanmar, Laos, Cambodia, the UAE, and the Philippines. Meta also suspended two million scam compound accounts last year.
** Malicious Chrome extensions behind WhatsApp spam: ** A cluster of malicious Chrome extensions is injecting code into the WhatsApp web client to send spam messages. The cluster includes 131 extensions with an install base of almost 21,000 users. The extensions are mainly targeting Brazilian users. Socket Security says it notified Google, but the extensions are still available on the official Chrome Web Store.
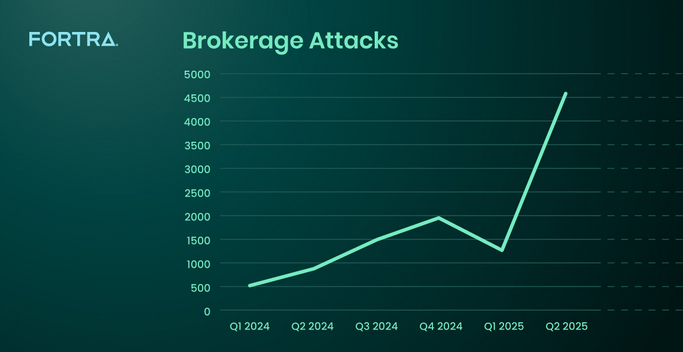
** Brokerage accounts under fire: ** Fortra has recorded a spike this year in threat actors targeting online brokerage accounts. The company has linked some of the attacks to Chinese cybercrime group, the Phishing Triad.
** Malware technical reports **
** New Mirai variant: ** Point Wild researchers have uncovered a new variant of the Mirai IoT malware that’s been distributed in the wild since June this year.
** Tykit: ** ANY.RUN looks at Tykit , a new phishing kit sold online and focusing on phishing Microsoft accounts.
** Lumma infostealer: ** Genians has published a technical report on the Lumma infostealer , the top stealer over the past year.
** Vidar Stealer 2.0 released: ** The developers of the Vidar Stealer have released v2.0 of the infostealer, taking advantage of a recent dox and dip in activity from the Lumma Stealer. According to Trend Micro , the malware is completely rewritten in C and can bypass most of the recent browser security features.
- In this sponsored product demo, ** Dropzone ** founder and CEO Edward Wu walks Risky Business podcast host Patrick Gray through the company’s AI SOC analyst. *
** APTs, cyber-espionage, and info-ops **
** China Time Service hack involved Triangulation: ** According to a technical report from China’s CERT , the NSA allegedly used the Triangulation iOS exploit to breach the phones of employees at the country’s National Time Service Center. This story broke over the weekend, and we featured it in our last edition, but I somehow missed the report it was based on.
** Salt Typhoon’s SnappyBee: ** DarkTrace has published a report on Salt Typhoon’s SnappyBee malware, also known as Deed RAT.
** PassiveNeuron targets MSSQL servers: ** A mysterious new APT group has targeted MSSQL servers for espionage purposes since June of last year. The PassiveNeuron attacks have targeted the servers of government and financial institutions in Asia, Africa, and Latin America. The group exploited vulnerabilities in the MSSQL database, its underlying servers, and brute-forced accounts that used weak passwords. The group later deployed two new backdoors tracked as Neursite and NeuralExecutor.
** BeaverTrail job interview campaign: ** Deriv security researcher Shantanu Ghumade looks over a clever “LinkedIn job interview” campaign that’s targeting AI engineers with some clever malware cocktail. The final payload is BeaverTrail, a backdoor historically linked to North Korean state-sponsored hackers.
** Russian info-ops targeting Poland: ** Google’s threat intel team looks at three Russian info-ops groups that leveraged Russia’s drone incursions in Poland to target the country’s population with information operations meant to blame the incidents on NATO, sow distrust against the local government, and promote a positive image of Russia.
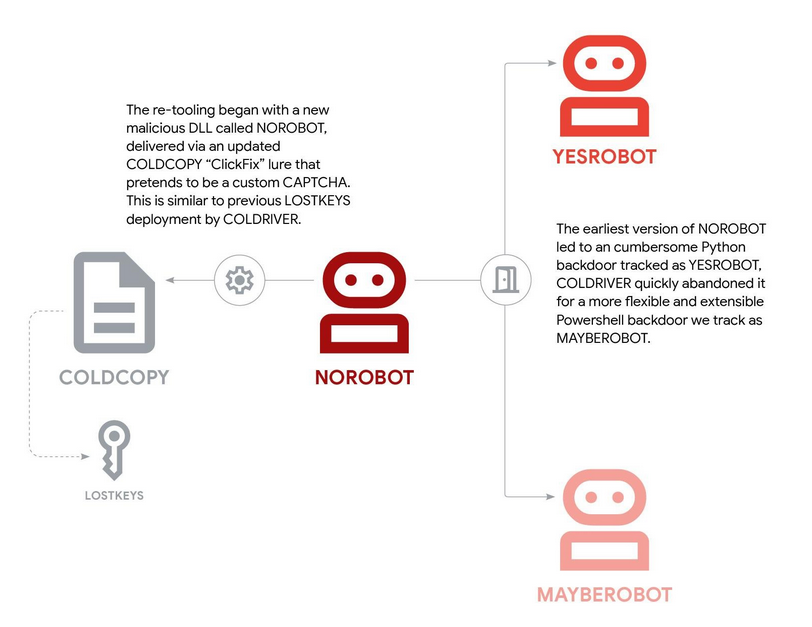
** ColdRiver’s ROBOT family: ** Google looks at YESROBOT, NOROBOT, and MAYBEROBOT , three new backdoors used by the Russian APT group ColdRiver in recent operations, typically deploying them via ClickFix campaigns.
** Vulnerabilities, security research, and bug bounty **
** KEV update: ** CISA has updated its KEV database with five vulnerabilities that are currently exploited in the wild. This includes two Kentiko CMS bugs, a second Oracle EBS vulnerability, a 2022 Apple bug, and a Windows SMB flaw from June.
** Zyxel security updates: ** Zyxel has released a security update to patch CVE-2025-8078 and CVE-2025-9133 . Both issues were discovered by Alessandro “RainPwn” Sgreccia and documented on his blog.
** Better Auth API minting vulnerability: ** A vulnerability in the BetterAuth authentication framework can allow attackers to mint API keys with elevated privileges for any user. The vulnerability (CVE-2025-61928) impacts a framework plugin that lets developers build authentication systems where users log in using API keys. According to ZeroPath , exploitation involves a single unauthenticated POST request sent to an app.
** Mercku router vulnerabilities: ** Multiple unpatched vulnerabilities are exposing Mercku router owners. The security bugs can allow attackers to reset passwords and run malicious code on the devices. The bugs are still unpatched a year after a security researcher notified the company. Mercku also didn’t reply to security researchers who notified the company that its support portal was hacked in June last year.
** TARmageddon vulnerability: ** A vulnerability in the async-tar Rust library can enable remote code execution attacks. Tracked as CVE-2025-62518, the vulnerability has been nicknamed TARmageddon and can allow threat actors to overwrite configuration files and hijack sensitive backends. The security flaw has a wide impact due to the large number of packages that have incorporated its code.
** Microsoft Minifilter write-up: ** Exodus Intelligence has published a technical write-up on an EoP in the Microsoft Cloud Files Minifilter driver, a driver used to sync to the Microsoft cloud. This was patched this month as CVE-2025-55690 .
** Microsoft Copilot exfil abuse: ** Security researcher Adam Logue has found a way to abuse Microsoft 365 Copilot mermaid diagrams to exfil data from targeted environments.
** Infosec industry **
** Threat/trend reports: ** CrowdStrike , Curator , KELA , Mondoo , and Omega Systems have recently published reports and summaries covering various threats and infosec industry trends.
** New tool—SetupHijack: ** UK security firm Hacker House has released SetupHijack , a tool that exploits race conditions and insecure file handling in Windows applications installer and update processes.
** New tool—BadTakeover-BOF: ** SpecterOps’ Logan Goins has released BadTakeover-BOF , a new tool to execute BadSuccessor dMSA privilege escalation and account takeover attacks, even on patched Windows Server 2025 systems.
** New tool—People on the Move: ** Something that I’m ashamed I discovered only now is SecurityWeek’s People on the Move section, a portal for tracking major infosec industry hires.
** Acquisition news #1: ** AI threat and risk intelligence company Dataminr has acquired fellow threat intel company ThreatConnect.
** Acquisition news #2: ** Backup company Veeam has acquired AI security firm Securiti.
** F1 sponsorship update: ** There’s this weird fetish in the infosec world with companies rushing to sponsor F1 teams. On that front, Bitdefender has extended its Ferrari sponsorship for three more years, through the 2028 F1 season.
** Boy Scouts cybersecurity badges: ** Scouting America (formerly Boy Scouts) has announced two new merit badges for AI and cybersecurity achievements. Members can gain the badges by passing the organization’s new AI and cybersecurity training courses. Boy Scouts can receive the new cybersecurity badge after learning how to spot malware and phishing emails, learning to set strong passwords, using firewalls, and more.
 via Scouting America, CNN
via Scouting America, CNN
** * Risky Business podcasts * **
-
In this edition of ** Between Two Nerds ** , Tom Uren and The Grugq talk to Joe Devanny, senior lecturer from King’s College London, all about India’s missing cyber power. It has the ingredients to become a cyber superpower, but so far, it hasn’t shown the motivation. *
-
In this edition of ** Seriously Risky Business ** , Tom Uren and Amberleigh Jack talk about First Wap, a Jakarta-based company that is selling surveillance-as-a-service. The good news is that it appears that government and media attention have had an impact on high-profile spyware vendors like NSO Group. The bad news is that these smaller players are flying under the radar and aren’t afraid of selling to sketchy customers. *