Welcome to Day One of Pwn2Own Automotive 2026! Today, 30 entries are taking the Pwn2Own stage to target the latest automotive systems, as the world’s top security researchers push technology to its limits. Exploits, surprises, and breakthrough discoveries are already unfolding - follow along here for updates throughout the day as the competition continues.
Stay up to date by following us on Twitter, Mastodon, LinkedIn, and Bluesky, and join the conversation using #Pwn2Own Automotive and #P2OAuto for continuous coverage.
FAILURE - Unfortunately, Team Hacking Group targeting Kenwood DNR1007XR in the In-Vehicle I…
Welcome to Day One of Pwn2Own Automotive 2026! Today, 30 entries are taking the Pwn2Own stage to target the latest automotive systems, as the world’s top security researchers push technology to its limits. Exploits, surprises, and breakthrough discoveries are already unfolding - follow along here for updates throughout the day as the competition continues.
Stay up to date by following us on Twitter, Mastodon, LinkedIn, and Bluesky, and join the conversation using #Pwn2Own Automotive and #P2OAuto for continuous coverage.
FAILURE - Unfortunately, Team Hacking Group targeting Kenwood DNR1007XR in the In-Vehicle Infotainment (IVI) category could not get their exploit working within the time allotted.
SUCCESS - Neodyme AG (@Neodyme) used a stack based buffer overflow to get a root shell on the Alpine iLX-F511, earning $20,000 USD and 2 Master of Pwn points.

SUCCESS - Fuzzware.io ( @ScepticCtf, @diff_fusion, @SeTcbPrivilege) chained two vulnerabilities (CWE-306, CWE-347) to achieve code execution on the Autel charger and manipulate the charging signal, earning $50,000 USD and 5 Master of Pwn points. Full win with the add-on.
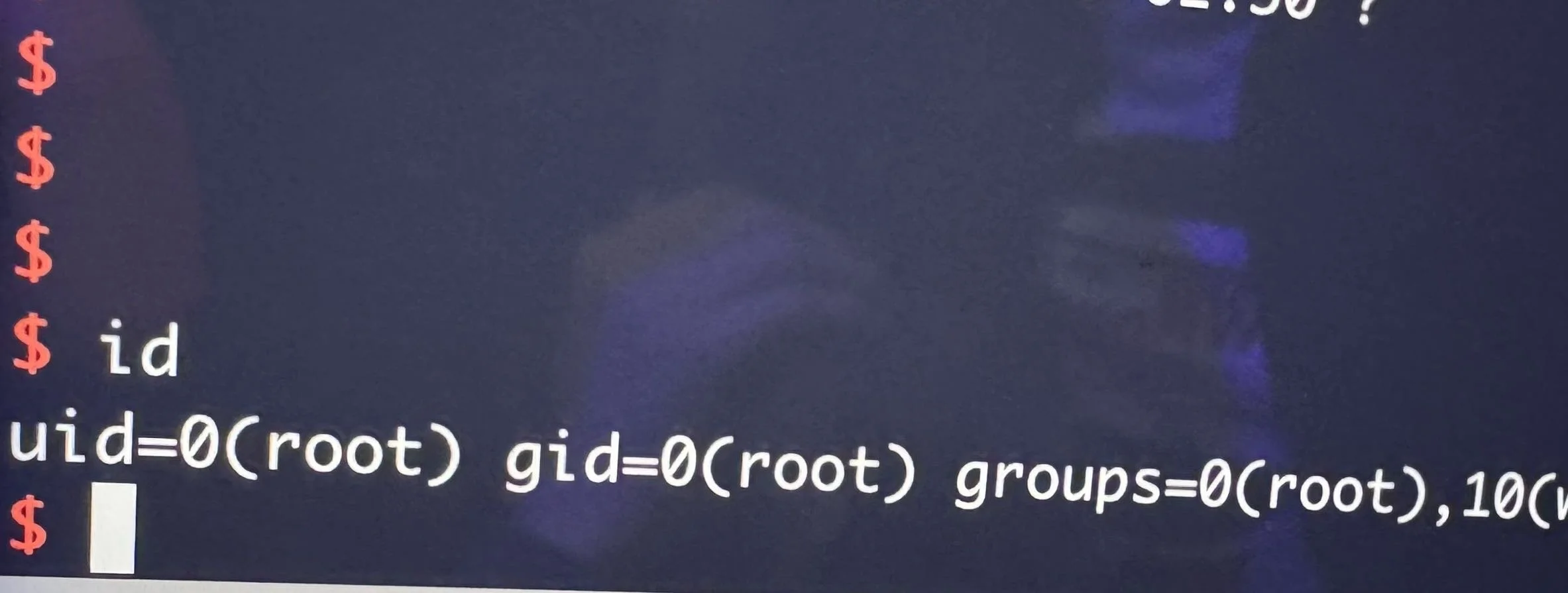
SUCCESS - Taejin Kim (@tae3), Junsu Yeo (@junactually), Sunmin Park (@sunminpark4503), Sungmin Son (@_ssm98), and Hoseok Lee of SKShieldus (@EQSTLab) of 299 exploited a hardcoded credential (CWE-798) to achieve code execution via CWE-494 on the Grizzl-E Smart 40A, earning $40,000 USD and 4 Master of Pwn points.
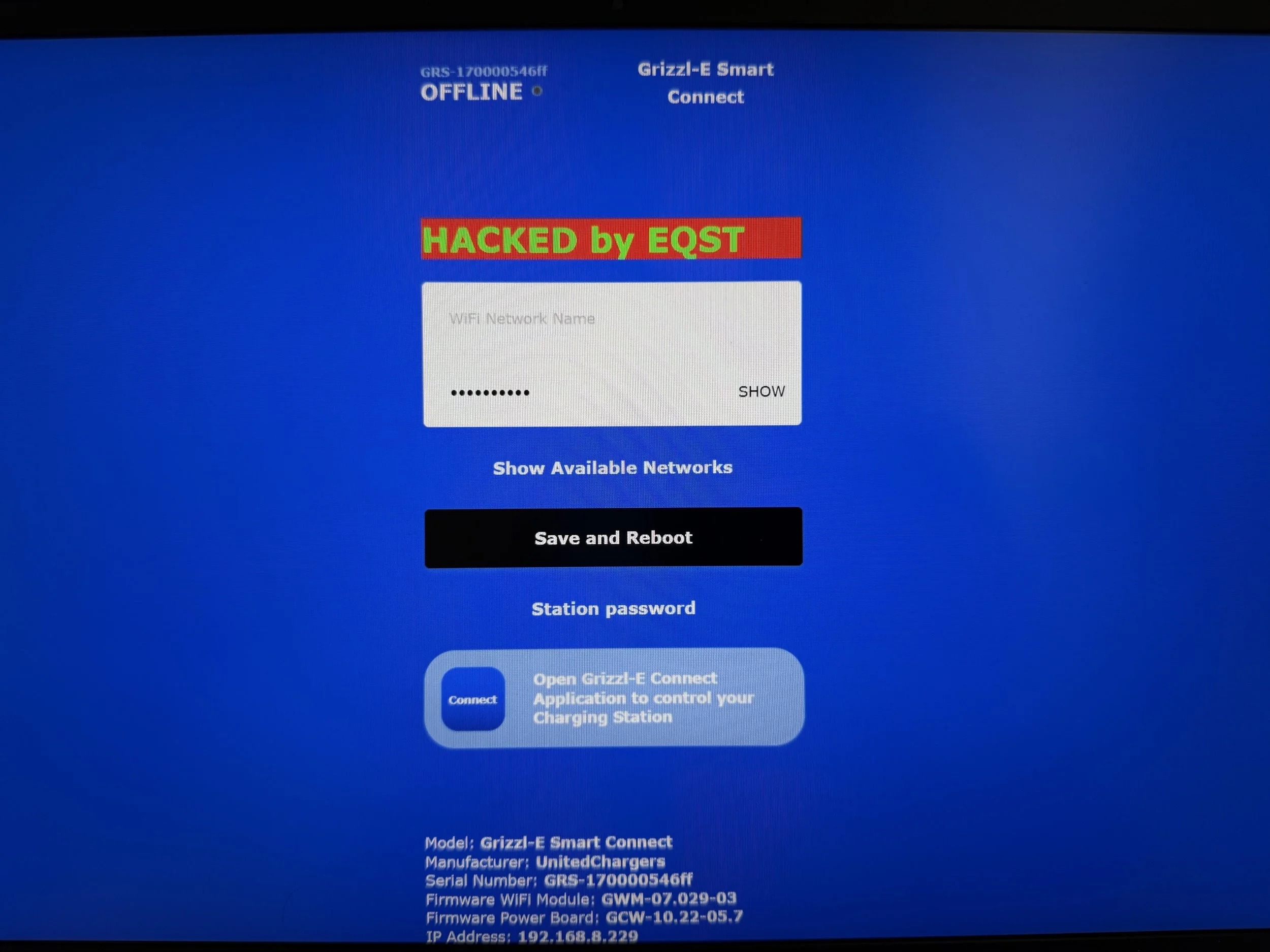
SUCCESS - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS exploited two bugs, including a command injection, against the ChargePoint Home Flex. Add-on failed, but still earned $40,000 USD and 4 Master of Pwn points.